Imagine a network where you can dynamically adjust security policies with a few clicks, responding instantly to emerging threats. That’s the promise of Software-Defined Networking (SDN), a revolutionary approach to network management. But, the inherent centralized control that makes SDN so powerful also presents a significant security challenge.
How do we ensure that this control plane itself doesn’t become a single point of failure, vulnerable to malicious attacks? This article delves into the crucial intersection of SDN and security, exploring how traditional security paradigms must evolve to protect these dynamic networks.
We’ll uncover the unique security vulnerabilities that SDN introduces, examine effective strategies for mitigating these risks, and explore cutting-edge solutions that leverage SDN’s programmability to enhance overall network security posture. Join us as we navigate the complex landscape of SDN security, providing you with the knowledge and insights to build truly resilient and protected next-generation networks.
SDN and Security: A New Era in Network Protection
Software-Defined Networking (SDN) has reshaped how we manage networks. But how does it affect security? Let’s dive into how SDN presents fresh ways to fortify your digital defenses.
Traditional network security often relies on hardware appliances. SDN offers a more flexible, programmable approach. This opens doors for innovative security strategies.
Imagine managing your network’s security posture from a central console. This is one of the core benefits of SDN, and we are here to find out what else it offers.
We’ll explore the strengths and challenges of using SDN to improve network security. We’ll touch on policy enforcement, threat detection, and incident response.
The Promise of Centralized Security Management
One of SDN’s key advantages is its centralized control. This makes managing security policies much simpler. Imagine making updates across your whole network in a single click.
Instead of configuring each device separately, security policies are applied globally. This reduces the chance of inconsistencies and misconfigurations. It’s about being fast and consistent.
The SDN controller acts as the brain of the network. It can monitor traffic, detect anomalies, and enforce security policies. It is like having a security guard in the control room.
Because we can monitor the traffic, it provides detailed insights into network activity. That aids in identifying potential threats, even those subtle ones.
Centralized logging and reporting become easier with SDN. That simplifies compliance efforts and improves the ability to track security events and any potential attacks.
Dynamic Threat Detection and Response
SDN’s programmability empowers dynamic threat response. When a threat is identified, the network can automatically adapt to mitigate the risk.
For instance, suspicious traffic can be instantly rerouted to a quarantine zone. This prevents the threat from spreading to other parts of the network and infecting sensitive data.
Firewall rules can be updated on the fly to block malicious IP addresses or ports. This provides a faster, more agile response than traditional methods. This response saves a lot of time.
SDN enables integration with threat intelligence feeds. This allows the network to proactively defend against known threats, as well as zero day attacks.
Think of it as an intelligent immune system for your network, always adapting and learning to fight off new challenges.
Micro-Segmentation for Enhanced Protection
SDN facilitates micro-segmentation, dividing the network into smaller, isolated zones. This limits the impact of a security breach. Segmentation contains the blast radius.
If one segment is compromised, the attacker cannot easily move laterally to other segments. This prevents a breach from becoming a full-blown catastrophe.
Micro-segmentation is particularly useful for protecting sensitive data. Data can be placed in a highly secured segment with restricted access and with strict protocols.
It also improves compliance with regulations that require data isolation. Meeting compliance becomes easier and saves resources on having audits done.
Each segment can have its own security policies, tailored to its specific needs and risk profile. This is a very nuanced and customized approach to security.
Challenges and Considerations
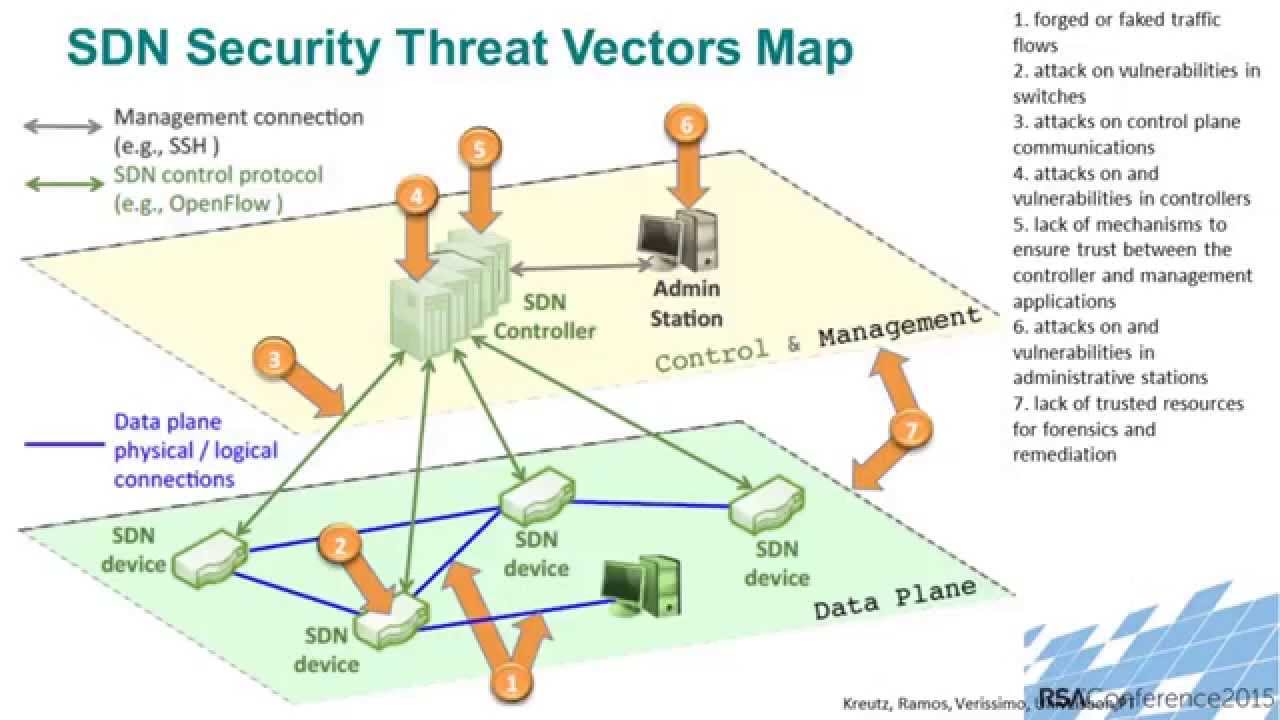
Implementing SDN security is not without its challenges. Skills are needed to implement it correctly.
Securing the SDN controller itself is paramount. If the controller is compromised, the entire network is at risk. It is the master key, so it must be kept safe.
Interoperability between different SDN vendors and technologies can be a hurdle. Ensuring compatibility is essential for a seamless implementation and easier scaling.
The complexity of SDN can make it difficult to troubleshoot security issues. It is recommended to have trained personnel or skilled consultants.
Organizations need to carefully plan their SDN security strategy. Careful planning is always needed when adopting new technologies.