In today’s digital landscape, a staggering number of cyberattacks occur every single day, each carrying the potential to cripple businesses, compromise sensitive data, and tarnish reputations. But how can organizations proactively defend themselves against these ever-evolving threats? The answer lies in a robust approach to risk assessment cybersecurity.
This process essentially involves identifying, analyzing, and evaluating potential vulnerabilities within a company’s digital infrastructure to determine the likelihood and impact of a successful cyberattack. It’s about understanding where you’re vulnerable, how severely you could be affected, and what steps you can take to mitigate those risks.
In this article, we’ll delve into the core components of a comprehensive risk assessment, exploring practical methodologies, common pitfalls to avoid, and actionable strategies to fortify your cybersecurity posture. Prepare to gain invaluable insights that will empower you to protect your valuable assets and navigate the complex world of cyber threats with confidence.
Understanding Cybersecurity Risk Assessments: A Practical Guide
Alright, let’s dive into cybersecurity risk assessments. Think of it as a health check for your digital world. We’re figuring out what could go wrong and how badly it could hurt.
It’s about being proactive, not reactive. Ignoring potential threats is like ignoring that weird engine noise in your car – eventually, it’ll leave you stranded. We want to avoid that digital breakdown.
A solid risk assessment identifies vulnerabilities, evaluates their impact, and helps you prioritize security measures. It’s a crucial piece of building a resilient digital defense.
This isn’t a one-time deal, either. The threat landscape is always shifting. Regularly revisiting your risk assessment ensures you’re staying ahead of emerging dangers and keeping safe.
Why Bother with Risk Assessments? The Benefits Unveiled
So, why dedicate resources to these assessments? Well, for starters, they offer a clear picture of your security posture. You’ll see the weak spots you didn’t know existed.
This knowledge allows you to make informed decisions about where to invest your security budget. Put your resources where they’ll have the biggest impact, and make it count!
Beyond budgeting, it helps you meet regulatory requirements. Many industries have specific security standards you must adhere to. Risk assessments help ensure compliance.
And let’s not forget about reputation. A data breach can severely damage your company’s image. Prevention, aided by these assessments, is significantly better than damage control.
Ultimately, a strong risk assessment process can improve overall confidence. Knowing you’ve diligently addressed potential threats gives peace of mind to leadership, and your customers.
The Core Components: What Makes Up a Risk Assessment?
A good risk assessment has a few key ingredients. First, we need to identify assets. These are the things you’re trying to protect: data, systems, networks, and even physical infrastructure.
Next, threat identification is crucial. This involves figuring out the possible dangers facing your assets, like malware, phishing attacks, or even disgruntled employees.
Then comes vulnerability analysis. Where are the weaknesses in your systems that those threats could exploit? Think unpatched software or weak passwords.
Finally, we need to assess the impact. If a threat exploits a vulnerability, how bad will it be? Will it be a minor inconvenience, or a catastrophic business disruption?
These components work together to create a comprehensive picture of your risk landscape. Each step builds upon the others, creating a useful and valuable end result.
Conducting a Risk Assessment: A Step-by-Step Approach
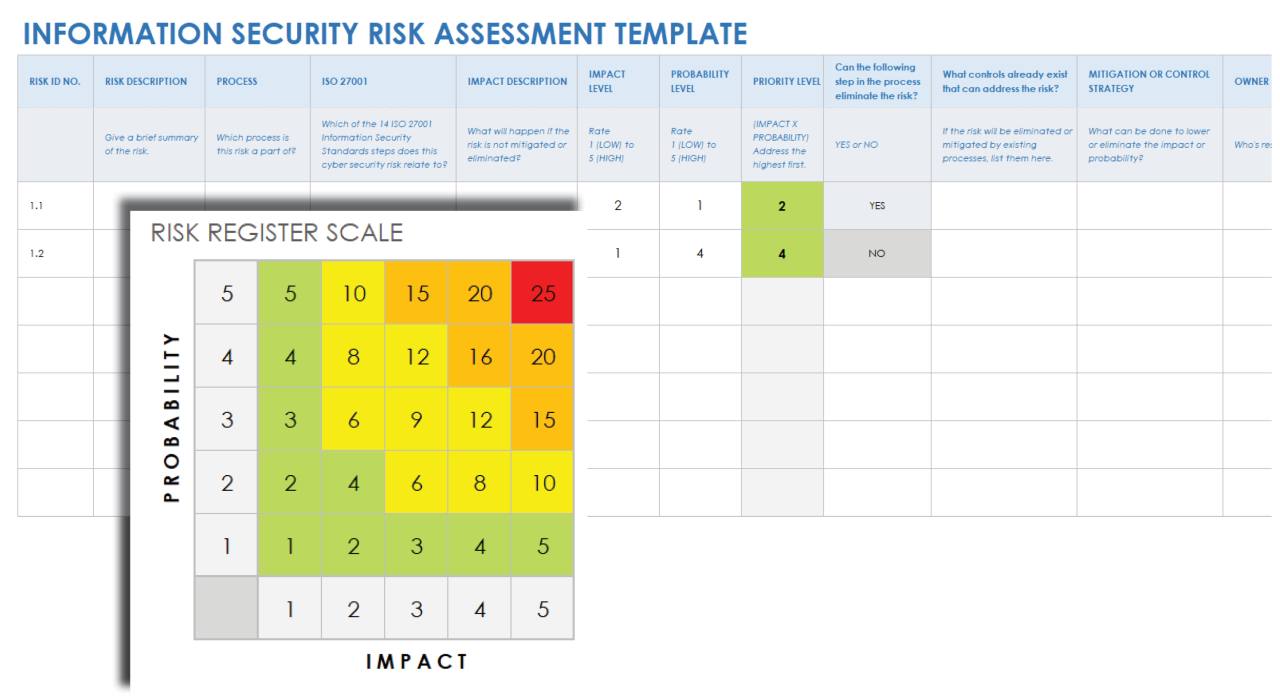
Ready to get started? First, define the scope of your assessment. What systems and data are you going to focus on? Be realistic and don’t try to boil the ocean.
Then, gather information. Interview key personnel, review existing security documentation, and use vulnerability scanning tools to identify weaknesses.
Next, analyze the data you’ve collected. Determine the likelihood of each threat occurring and the potential impact if it does. Use a risk matrix to visualize the results.
Develop a risk mitigation plan. What steps will you take to reduce or eliminate the identified risks? Prioritize actions based on the severity of the risk.
Finally, document everything. Create a report detailing your findings, recommendations, and mitigation plan. This document will be invaluable for future reference and audits.
Tools and Techniques: Making the Assessment Easier
There’s a wide array of tools available to help you with your assessment. Vulnerability scanners can automatically identify weaknesses in your systems.
Penetration testing simulates real-world attacks to see how well your defenses hold up. It’s like a dress rehearsal for a cyberattack, without the actual consequences.
Risk assessment frameworks, such as NIST or ISO, provide a structured approach to the process. They offer guidance and best practices to ensure you cover all the bases.
Using questionnaires and checklists can help you gather information from key stakeholders. Collaboration is critical for a comprehensive and accurate assessment.
Don’t underestimate the power of good old-fashioned brainstorming. Get your team together and discuss potential threats and vulnerabilities. Fresh perspectives can be invaluable.
Staying Ahead: Continuous Monitoring and Improvement
As mentioned earlier, a risk assessment isn’t a one-and-done thing. Cyber threats are constantly evolving, so your security measures need to adapt as well.
Implement continuous monitoring to detect new threats and vulnerabilities as they emerge. Automated security tools can help you stay on top of things.
Regularly review and update your risk assessment based on new information and changes in your environment. Re-evaluate risks, update the mitigation plan, and repeat.
Track the effectiveness of your mitigation efforts. Are your security controls actually reducing the risks you identified? If not, it’s time to make adjustments.
Embrace a culture of continuous improvement. Encourage employees to report security concerns and actively seek out ways to enhance your security posture. Knowledge is power!