Imagine your home without locks on the doors. Unthinkable, right? In the digital world, our networks and systems are equally vulnerable, constantly facing threats lurking in the shadows. That’s where intrusion detection software (IDS) comes in – your digital security guard, constantly monitoring for suspicious activity and raising the alarm before damage is done.
In today’s interconnected world, where data breaches make headlines daily and cyber threats evolve at lightning speed, understanding and effectively utilizing IDS is no longer optional; it’s essential for businesses and individuals alike. This article will delve into the core of intrusion detection software, exploring its different types, how it works, the challenges it presents, and most importantly, how to leverage it to bolster your defenses against the ever-present threat of cyberattacks.
Prepare to unlock the secrets to a more secure digital future.
Understanding Intrusion Detection Software: A Comprehensive Guide
In today’s interconnected digital world, security is paramount. Intrusion Detection Software (IDS) acts as a vigilant guardian, constantly watching over your systems. It identifies possible malevolent activities, sounding the alarm when something appears amiss.
This technology analyzes network traffic, system logs, and file integrity. When an anomaly arises, it triggers an alert. This process gives security teams a chance to investigate and respond swiftly.
Think of an IDS as a sophisticated burglar alarm for your digital assets. It doesn’t prevent intrusions, it detects them, empowering a rapid response. This article dives deep into the world of IDS, examining its components, types, and best practices.
This overview helps you determine how intrusion detection software can enhance your current security posture. Discover the crucial role it plays in a multifaceted cybersecurity strategy.
What is Intrusion Detection Software (IDS)?
Intrusion Detection Software (IDS) represents an invaluable asset to modern cybersecurity. It provides a crucial layer of threat detection. The software serves to monitor a network or system for harmful activities.
Unlike firewalls that prevent unauthorized access, IDS focuses on identifying suspicious behavior after it has already occurred. It works by analyzing network traffic, system logs, and other data sources.
By comparing observed activity to established patterns of malicious behavior or deviations from standard operational practices, the system flags potential threats. This proactive approach alerts security personnel to respond.
The main objective of an IDS is not to block or prevent attacks, but to identify and alert security teams to ongoing or successful breaches. This allows for swift incident response and minimizes the damage caused by intrusions.
Early threat identification allows prompt action. These actions can include isolating affected systems or patching vulnerabilities. This can stop the propagation of malicious activities and thwart extensive damage.
IDS is a critical component of a well-rounded cybersecurity strategy, complementing prevention measures such as firewalls. It is like a second line of defense.
Types of Intrusion Detection Systems
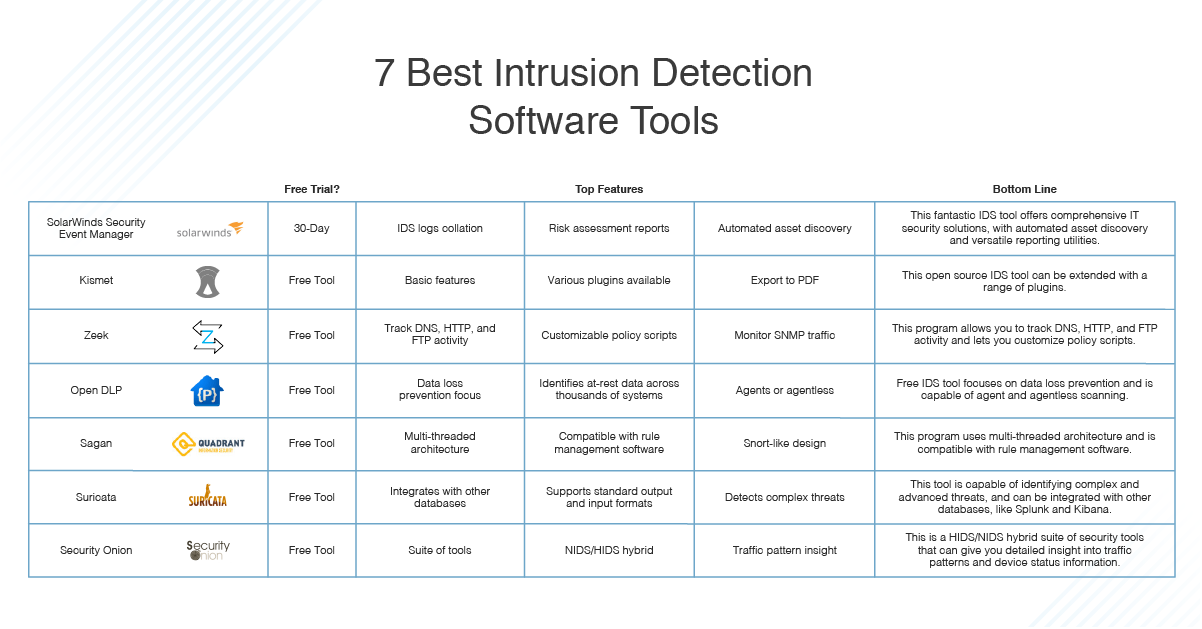
Intrusion Detection Systems come in diverse forms, each possessing unique strengths and deployment strategies. Choosing the right type depends on your organization’s specific requirements and threat landscape.
Network Intrusion Detection Systems (NIDS): NIDS monitor network traffic at strategic points. They analyze data packets for malicious patterns or anomalies. When suspicious activity is detected, the system triggers an alert.
Host Intrusion Detection Systems (HIDS): HIDS are installed on individual hosts or endpoints. These monitor system logs, file integrity, and process activity. They provide a detailed view of activity on specific machines.
Signature-Based IDS: This approach relies on a database of known attack signatures. It is like a digital fingerprint. When network traffic matches a known signature, the system flags it as a potential threat.
Anomaly-Based IDS: This method establishes a baseline of normal network or system behavior. Any deviation from this baseline is flagged as suspicious. This is particularly useful for identifying new or unknown threats.
Hybrid IDS: Many modern IDS solutions combine elements of multiple approaches. They may combine signature-based and anomaly-based detection. Hybrid IDS provides a more comprehensive and accurate view of the threat landscape.
How Intrusion Detection Software Works
IDS functions by constantly monitoring network traffic and system activity for suspicious patterns or deviations from normal behavior. The software uses a variety of techniques to identify possible threats.
First, the IDS collects data from various sources. These sources include network packets, system logs, and application activity. This data provides the raw material for analysis.
Next, the IDS analyzes the collected data using a combination of methods. Signature-based detection compares the data to a database of known attack signatures. Anomaly-based detection looks for deviations from established baselines.
When the IDS detects suspicious activity, it generates an alert. This alert is sent to security personnel for investigation. The alert provides information about the nature of the potential threat, its source, and its target.
Security teams then analyze the alerts, determining whether a real threat is present. Based on the analysis, they can take appropriate actions. Actions might include isolating affected systems, blocking malicious traffic, or patching vulnerabilities.
The core function of IDS lies in continuous monitoring, analysis, and alert generation. This empowers rapid incident response to mitigate the impact of harmful activities.
Benefits of Using Intrusion Detection Software
Implementing intrusion detection software brings a multitude of benefits to organizations. It contributes to a more robust and responsive security posture. One of the most important perks is improving your security.
Enhanced Threat Detection: IDS provides continuous monitoring and analysis of network and system activity. This helps detect potential threats that may bypass other security controls.
Improved Incident Response: By generating alerts when suspicious activity is detected, IDS enables security teams to respond quickly and effectively to incidents. This can minimize the damage caused by intrusions.
Compliance Requirements: Many regulatory frameworks require organizations to implement intrusion detection or prevention measures. Using IDS can help organizations meet these compliance requirements.
Early Warning System: IDS acts as an early warning system, alerting security teams to potential threats before they cause significant damage. This allows for proactive remediation and prevents escalation.
Valuable Security Insights: The data collected by IDS can provide valuable insights into the types of attacks targeting your organization. This intelligence can inform future security strategies.
Best Practices for Implementing Intrusion Detection Software
To maximize the effectiveness of IDS, it’s crucial to adhere to certain best practices during implementation and ongoing management. Proper planning will always benefit your organization in the long run.
Define Clear Objectives: Clearly define your goals. Determine what you want to achieve with your IDS deployment. This helps in selecting the right type of IDS and configuring it effectively.
Proper Placement: Strategically place your IDS sensors or agents. Focus on locations where they can effectively monitor critical network segments and systems. This ensures thorough coverage.
Regular Updates: Maintain your IDS software with the latest signature updates and security patches. Staying current helps to detect and mitigate emerging threats. Outdated software leaves you exposed.
Fine-Tuning and Configuration: Customize your IDS configuration to match your specific environment. Reduce false positives by tuning detection thresholds and excluding benign traffic. Don’t blindly follow default settings.
Incident Response Plan: Develop a clear incident response plan. This outlines the steps to take when the IDS generates an alert. A well-defined plan ensures a coordinated and effective response.
Continuous Monitoring and Analysis: Continuously monitor IDS alerts. Analyze the data to identify trends and patterns. Use this information to improve your security posture.