In today’s hyper-connected world, a staggering number of cyberattacks occur every single day, costing businesses of all sizes billions of dollars and irreparable reputational damage. Are you confident your organization is adequately prepared to weather the inevitable storm? Cybersecurity risk management isn’t just about installing firewalls and antivirus software; it’s a comprehensive process of identifying, assessing, and mitigating the ever-evolving threats that target your digital assets.
It’s the proactive strategy that separates those who survive a cyberattack from those who become another statistic. This article delves into the core principles of cybersecurity risk management, offering practical insights and actionable strategies to help you understand your organization’s vulnerabilities, prioritize your defenses, and ultimately build a more resilient security posture.
From understanding the risk management framework to implementing effective mitigation strategies, we’ll equip you with the knowledge to navigate the complex landscape of cyber threats and protect what matters most.
Cybersecurity Risk Management: A Practical Guide
Navigating the digital world requires more than just strong passwords. Understanding and managing cybersecurity risks is essential for individuals and organizations alike. It’s about proactively protecting valuable assets from evolving digital threats.
This article provides a practical guide to cybersecurity risk management, offering actionable strategies to bolster your defenses. We’ll explore the core principles and steps involved in building a robust security posture.
Think of it as a roadmap for securing your digital landscape. The goal is to minimize vulnerabilities and create a resilient environment that can withstand potential attacks.
Let’s dive into the details of this critical discipline. We will cover identifying threats, assessing impact, and mitigating exposures to protect what matters most.
Understanding Cybersecurity Risks
Cybersecurity risks are potential dangers that exploit vulnerabilities in systems, networks, and applications. These exposures can lead to data breaches, financial losses, and reputational damage.
Risks can come in various forms, from malware and phishing attacks to insider threats and denial-of-service assaults. Each poses a unique challenge to your security framework and calls for tailored responses.
The landscape of threats is ever-changing, with new vulnerabilities and attack vectors emerging continuously. Staying informed and adapting your safeguards is a cornerstone of sound risk management.
Recognizing and understanding these potential hazards is the first step in formulating an effective defense strategy. Ignoring them can leave you exposed to significant consequences.
Consider the potential impact of ransomware encrypting critical business data, halting operations. Or the damage inflicted by a data breach exposing customer information, eroding trust.
The Cybersecurity Risk Management Process
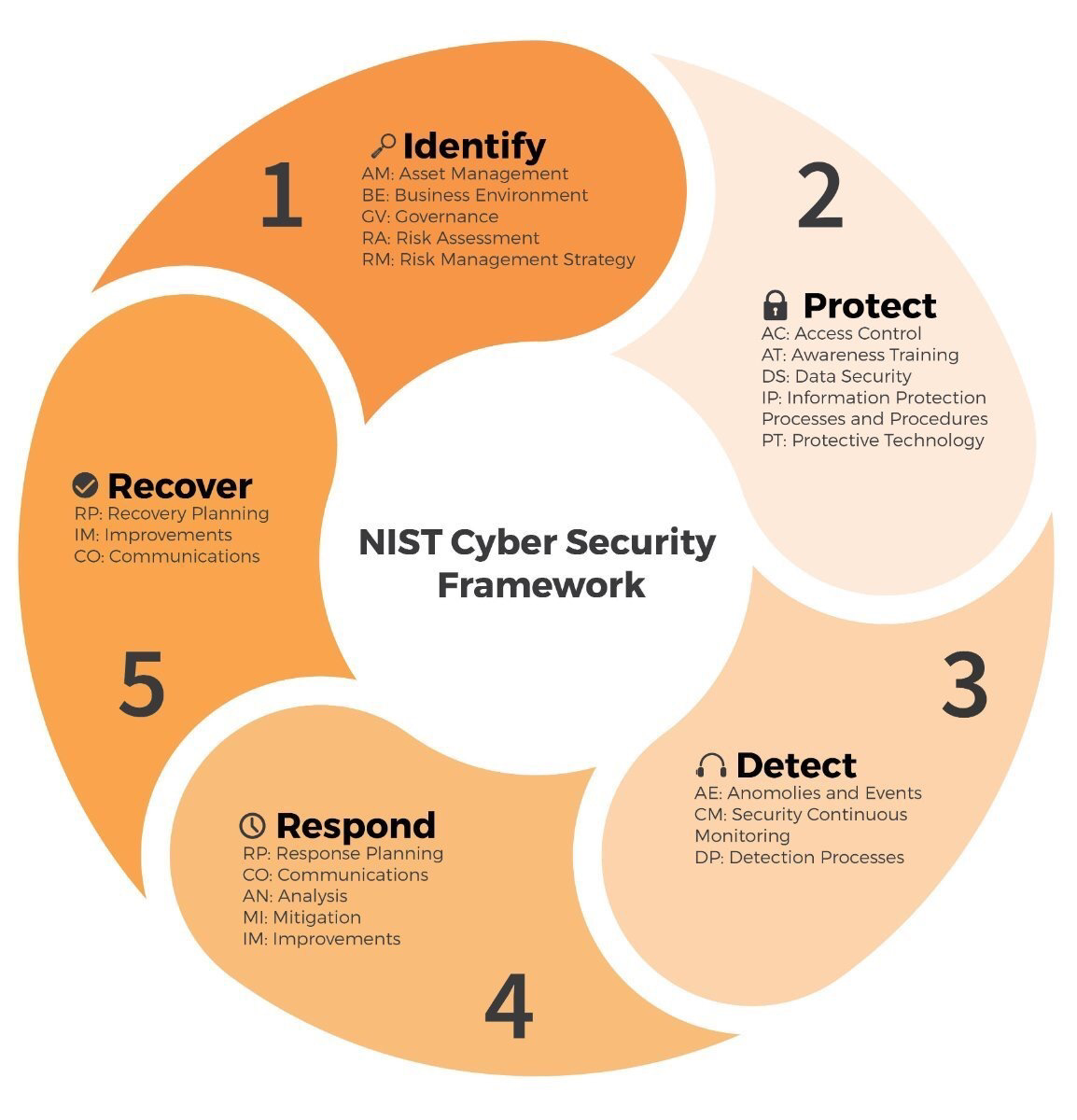
Risk management is not a one-time fix but an ongoing process involving identification, assessment, mitigation, and monitoring. It is a circular, iterative process that constantly adapts to new threats.
First, Identify potential risks by cataloging vulnerabilities and assessing likely threats. Next, Assess the impact and likelihood of each identified risk to prioritize response efforts.
Mitigate identified risks by implementing controls and countermeasures. This could include things like enhanced data encryption, more training, or even stronger policies and procedures.
Finally, Monitor the effectiveness of these controls and adapt your strategy as needed, making adjustments based on current threats and emerging risks.
Regularly reviewing and updating your risk management plan is crucial. The digital landscape is dynamic, and your protections must evolve to keep pace with emerging exposures.
Identifying Cybersecurity Risks
Identifying vulnerabilities starts with a comprehensive assessment of your systems, networks, and applications. This may involve tools like vulnerability scanners and penetration testing.
Consider both internal and external threats, analyzing potential attack vectors and weaknesses in your security architecture. Don’t just focus on technology, consider the people factor.
Examine policies and procedures to identify gaps or vulnerabilities that could be exploited by malicious actors. Social engineering is often the first step toward data breaches.
Keep an eye on industry news and threat intelligence reports to stay informed about emerging risks. Knowing what others are facing can give you a head start on preparing for new risks.
Don’t forget physical security. A breach of physical access can provide a gateway to digital systems, circumventing digital protections. Review cameras, badges and monitoring.
Assessing Cybersecurity Risks
Assessment involves evaluating the potential impact and likelihood of each identified risk. This helps prioritize which exposures require the most urgent attention and resources.
Impact assessment considers the financial, operational, and reputational consequences of a successful attack. How much would it cost to recover from ransomware, or the impact to brand reputation?
Likelihood assessment estimates the probability of a specific threat exploiting a particular vulnerability. How likely is it that a given vulnerability will be exploited by malicious actors?
Risk matrices are often used to visualize and prioritize risks based on their impact and likelihood. This gives leadership and managers the information needed to make decisions.
Quantitative risk assessment uses numerical data to quantify potential losses. Qualitative assessment relies on expert judgment and subjective evaluations. The method depends on company needs.
Mitigating Cybersecurity Risks
Mitigation involves implementing controls to reduce the likelihood or impact of identified risks. This can include technical, administrative, and physical safeguards.
Technical controls might include firewalls, intrusion detection systems, and encryption. Encryption can protect sensitive data at rest and in transit.
Administrative controls involve policies, procedures, and training programs. Employee training on phishing awareness is a crucial safeguard, creating a human firewall.
Physical controls include security cameras, access control systems, and environmental protections. Limiting physical access to data centers and server rooms enhances security.
Consider implementing a multi-layered approach to security, combining multiple safeguards to provide defense in depth. No single solution guarantees absolute security.