Imagine your home – you wouldn’t leave the doors and windows unlocked, would you? In the digital world, our networks and systems are our homes, and cyber security vulnerability assessments are the security checks that ensure everything is locked up tight.
These assessments are a critical process of identifying, quantifying, and prioritizing the vulnerabilities within a system. Failing to conduct them regularly can leave your organization exposed to cyberattacks, data breaches, and significant financial losses. This article will delve into the core principles of cyber security vulnerability assessments, exploring the various methodologies, tools, and best practices employed to protect your digital assets.
We’ll unravel the complexities and show you how a proactive approach to identifying and mitigating weaknesses can significantly enhance your overall security posture, giving you the knowledge to confidently navigate the ever-evolving cyber threat landscape and keep your digital “house” secure.
Cyber Security Vulnerability Assessment: Finding the Cracks Before They Break
Alright, let’s talk about vulnerability assessments. In the cybersecurity world, this is like giving your digital fortress a thorough health checkup. It’s all about pinpointing weaknesses before the bad guys do. Think of it as preventative medicine for your systems.
A vulnerability assessment goes beyond just surface-level checks. We’re diving deep to uncover potential vulnerabilities, those hidden doors and windows that could let attackers in. It helps you understand your risk landscape so you can proactively defend.
Why is this so crucial? Well, in today’s interconnected world, threats are constantly evolving. A vulnerability assessment ensures your defenses are up-to-date and effective against the latest attack techniques. Staying ahead is the name of the game.
Ultimately, these assessments provide the insights needed to prioritize security efforts. Instead of spreading resources thin, you can focus on the areas that need the most attention. It’s about making smart, informed decisions about your security posture.
Why You Need a Vulnerability Assessment
Simple: to keep your data safe and your operations running smoothly. Data breaches can be catastrophic, costing companies significant amounts of money and damaging their reputation. Assessments mitigate this risk.
Compliance is another big factor. Many regulations, like HIPAA and PCI DSS, require organizations to conduct vulnerability assessments. Staying compliant avoids hefty fines and legal headaches down the road.
Consider the value of customer trust. A security breach can erode that trust quickly, leading to loss of customers and revenue. Proactive vulnerability assessments demonstrate a commitment to security that can boost confidence.
And let’s not forget about efficiency. By identifying and addressing vulnerabilities early, you can prevent costly incidents that could disrupt your business. It’s an investment that pays off in the long run by preventing downtime.
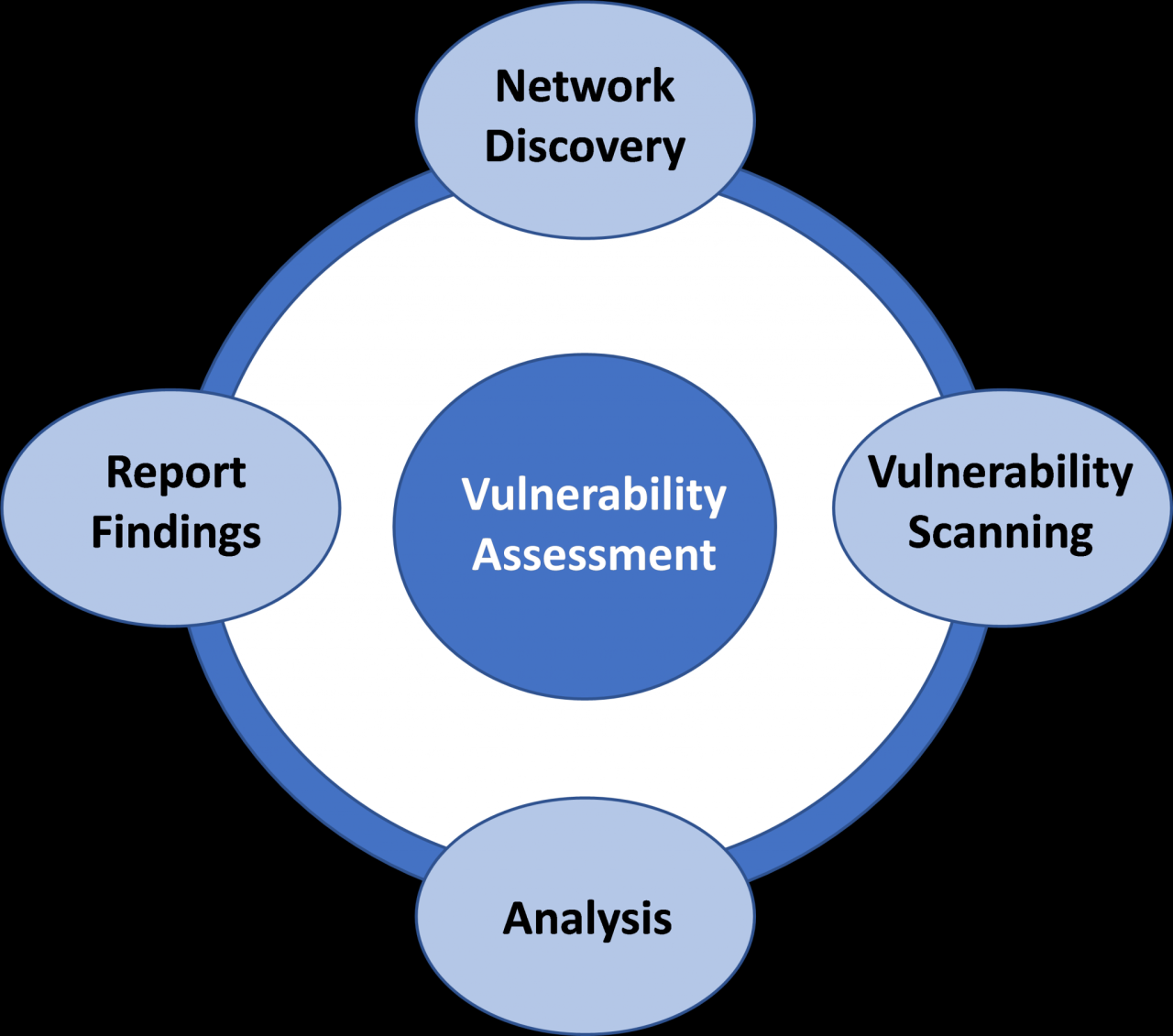
The Vulnerability Assessment Process: A Step-by-Step Guide
First, it begins with scope definition. You need to determine which systems, networks, and applications will be included in the assessment. This sets the boundaries for the entire operation.
Next is vulnerability scanning. Automated tools are used to identify known vulnerabilities in the defined scope. This is where the tools really earn their keep. It’s important to use various tools for wider coverage.
After the scan, vulnerability analysis comes into play. The findings from the scan are reviewed and validated. False positives are weeded out, and the severity of each real vulnerability is assessed to focus on what matters.
Then comes reporting. A comprehensive report is created, detailing the identified vulnerabilities, their potential impact, and recommended remediation steps. This report forms the basis for your security improvement plan.
Finally, we look at remediation. Addressing identified vulnerabilities, often through patching, configuration changes, or code updates. After this is done, a re-scan is recommended to ensure effectiveness.
Types of Vulnerability Assessments
There are several types, each focusing on a different area. A network vulnerability assessment examines your network infrastructure for weaknesses that could be exploited. Think routers, firewalls, and servers.
Web application vulnerability assessments focus specifically on web applications. These can uncover vulnerabilities like SQL injection and cross-site scripting (XSS) – common attack vectors against online services.
A host-based vulnerability assessment examines individual systems, like desktops and laptops, for vulnerabilities. These assessments often check for missing patches and insecure configurations.
Finally, database vulnerability assessments target databases, seeking out weak credentials, unpatched software, and other vulnerabilities that could compromise sensitive data. Security starts at the foundation.
Tools of the Trade: Common Vulnerability Assessment Tools
Several tools are used for vulnerability assessments, each with its strengths. Nessus is a popular commercial scanner known for its comprehensive vulnerability database and ease of use. It’s a good all-around option.
OpenVAS is a free and open-source scanner that provides similar functionality to Nessus. It’s a great option for organizations looking for a cost-effective solution. It provides great insight if used correctly.
Qualys is a cloud-based vulnerability management platform that offers a wide range of features, including vulnerability scanning, asset tracking, and compliance reporting. Good for centralizing all activity.
And, Burp Suite is a widely used tool for web application security testing. It allows you to intercept and manipulate web traffic, identify vulnerabilities, and test the security of your web applications.
Making the Most of Your Vulnerability Assessment
First, prioritize remediation based on risk. Focus on vulnerabilities that pose the greatest threat to your most critical assets. Don’t just patch everything at once; be strategic.
Automate assessments to ensure regular and consistent monitoring. Continuous scanning is crucial for staying ahead of emerging threats. Set up a schedule and stick to it.
Integrate your vulnerability assessment process with other security tools and processes. Share information and coordinate efforts to create a more comprehensive security posture. Make security the whole goal.
Finally, train your staff on security best practices. Human error is a major cause of security breaches, so educating your team is essential. People are the first line of defense.