Did you know that a single data breach can cost a company millions, not just in fines, but also in lost business and irreparable damage to its reputation? In today’s digital landscape, where data is the lifeblood of every organization, cybersecurity isn’t just a technical concern; it’s a critical business imperative.
But simply having security measures in place isn’t enough. Organizations must also navigate the complex world of cybersecurity compliance – adhering to a patchwork of regulations and standards designed to protect sensitive information. Think of it as the rules of the road for data security, ensuring that your organization is operating safely and responsibly online.
This article will unpack the essentials of cybersecurity compliance, demystifying the key regulations, highlighting common challenges, and providing practical guidance on how to build a robust compliance program that not only safeguards your data but also protects your bottom line and builds trust with your customers.
Prepare to discover how to turn compliance from a burden into a business advantage.
Cyber Security Compliance: Navigating the Digital Maze
In today’s hyper-connected world, cyber security compliance isn’t just a good idea; it’s vital. Think of it as your digital insurance policy, protecting your valuable data and reputation.
Failure to comply with regulations can lead to hefty penalties, damaged credibility, and loss of customer trust. It’s a complex landscape, but understanding the basics is crucial.
This guide will simplify cyber security compliance, providing insights and practical steps to keep your organization safe and compliant. Let’s explore the key aspects together.
Essentially, cyber security compliance means adhering to a set of rules, standards, and laws designed to protect sensitive information from unauthorized access, use, disclosure, disruption, modification, or destruction.
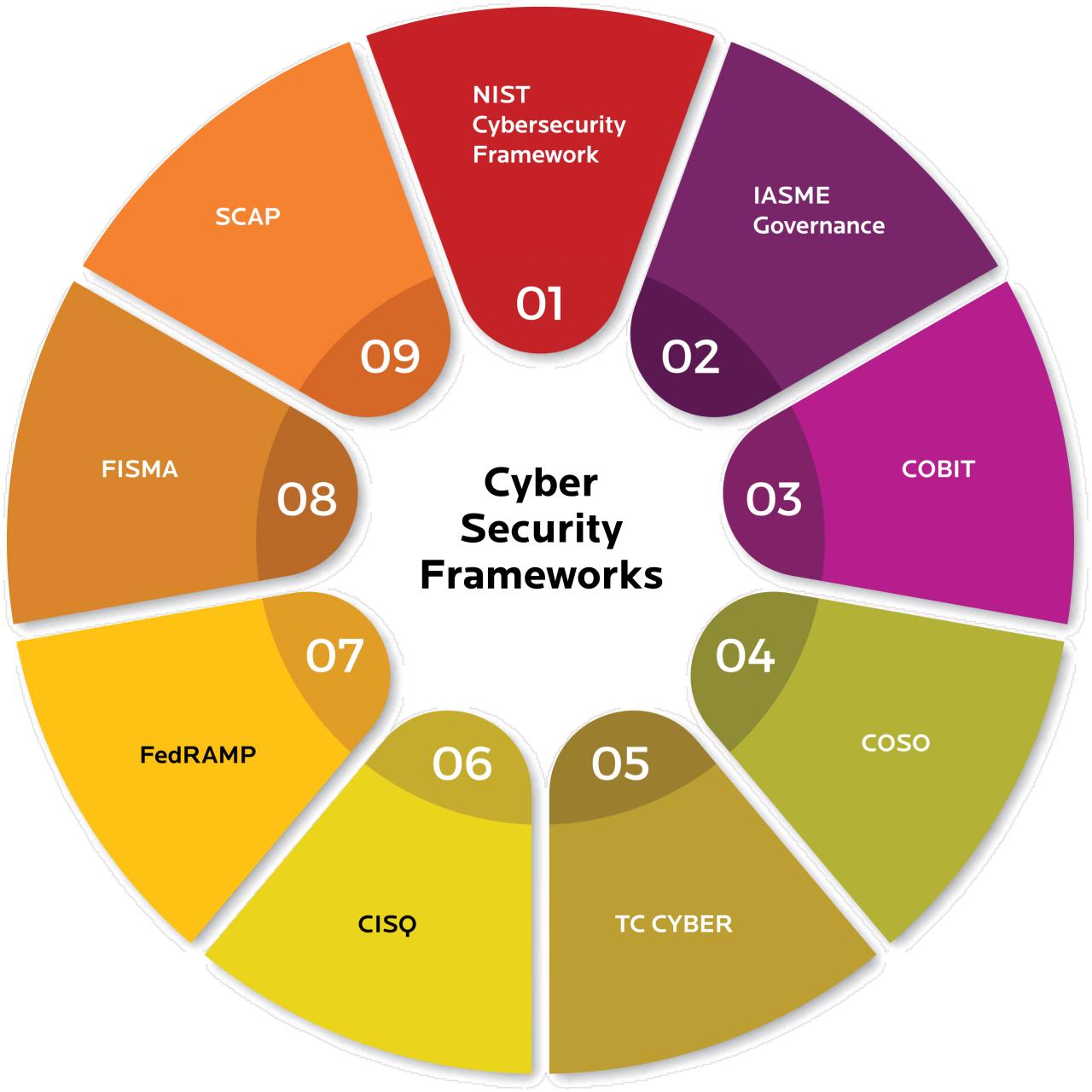
Understanding Key Cyber Security Compliance Frameworks
Several frameworks dictate cyber security best practices. Familiarizing yourself with these is the first step toward effective compliance. Each framework has different requirements.
PCI DSS (Payment Card Industry Data Security Standard): This applies to any organization that handles credit card information. Protecting cardholder data is its primary goal.
HIPAA (Health Insurance Portability and Accountability Act): This US law protects sensitive patient health information. Covered entities and their business associates must comply.
GDPR (General Data Protection Regulation): This EU regulation governs the processing of personal data of individuals within the European Union. It has global implications for organizations processing EU citizens’ data.
NIST Cybersecurity Framework: A voluntary framework based on existing standards, guidelines, and practices to manage cyber security risk. Widely adopted across industries.
These frameworks all help organizations to better understand and manage risks to their IT systems, and implementing them can help companies to prevent serious issues from happening.
Steps to Achieve Cyber Security Compliance
Achieving cyber security compliance is a journey, not a destination. It requires ongoing effort and commitment from all levels of an organization. Where does one even begin?
Risk Assessment: Identify your organization’s vulnerabilities and potential threats. Understanding your weaknesses is paramount.
Policy Development: Create clear, comprehensive cyber security policies and procedures. Make sure these are easy to understand and follow.
Implementation: Implement security controls and technologies to mitigate identified risks. This might involve firewalls, intrusion detection systems, or encryption.
Training and Awareness: Educate employees about cyber security threats and best practices. Human error is a significant factor in many breaches.
Monitoring and Auditing: Continuously monitor your systems for security incidents and conduct regular audits to ensure compliance. Stay vigilant.
Incident Response: Develop a plan for responding to security incidents. Time is of the essence during a breach.
By following these steps, an organization is much more likely to remain compliant with the various legal requirements they must meet.
The Role of Technology in Cyber Security Compliance
Technology plays a crucial role in achieving and maintaining cyber security compliance. Various tools and solutions can automate tasks and enhance security posture.
Security Information and Event Management (SIEM) systems: These aggregate and analyze security data from across your network, providing real-time threat detection.
Vulnerability Scanners: These identify weaknesses in your systems before attackers can exploit them. Proactive detection is key.
Data Loss Prevention (DLP) solutions: These prevent sensitive data from leaving your organization’s control. Protecting data is paramount.
Encryption: Protects data at rest and in transit. Essential for data security.
The correct technological choices can help ensure the policies and processes are followed correctly, but people and processes are even more important than just technology.
Common Cyber Security Compliance Challenges
Navigating the cyber security compliance landscape isn’t always easy. Organizations face various challenges. One common example is a lack of resources.
Lack of Resources: Implementing and maintaining compliance can be expensive. Many smaller firms do not have the funding to hire experts.
Complexity of Regulations: Keeping up with evolving regulations can be daunting. The legal world changes quickly.
Employee Resistance: Users may resist new security policies and procedures. Education and communication are essential.
Third-Party Risk: Ensuring the security of your vendors and partners is crucial. Supply chain attacks are increasingly common.
Budget limitations: Often, there are not enough funds in the budget to implement security compliance correctly and carefully.
The Future of Cyber Security Compliance
The future of cyber security compliance is likely to be shaped by emerging technologies and evolving threats. Prepare for changes. With AI advancing quickly, that is already starting to change things.
Increased Automation: AI and machine learning will automate many compliance tasks. Faster processes are important.
Greater Focus on Privacy: Privacy regulations will become more stringent. Individuals are increasingly concerned about their data.
Standardization of Frameworks: Efforts to standardize compliance frameworks will continue. A clearer playing field can help organizations.
Emphasis on Proactive Security: Organizations will shift from reactive to proactive security measures. Prevention is better than cure.