Are you confident that your data is truly secure in the cloud? With businesses increasingly relying on cloud infrastructure for everything from data storage to critical applications, the security of your cloud network has never been more paramount.
Cloud network security, in essence, is the implementation of policies, controls, procedures, and technologies to protect the integrity, confidentiality, and availability of data and resources residing within cloud environments. This isn’t just an IT concern; it’s a business imperative.
A single breach can lead to devastating financial losses, reputational damage, and legal repercussions. In this article, we’ll delve into the key challenges organizations face when securing their cloud networks, explore essential strategies for robust protection, and provide actionable insights to help you navigate the complex landscape of cloud security.
By the end, you’ll have a clearer understanding of how to safeguard your cloud environment and ensure the long-term resilience of your business.
Cloud Network Security: A Deep Dive
Cloud network security is no longer optional; it’s a necessity. As businesses shift their operations to the cloud, safeguarding data and applications becomes paramount. It’s about implementing strategies that prevent breaches, ensure compliance, and maintain customer trust.
This article unpacks the essentials of cloud network security. We’ll navigate through key concepts, discuss practical measures, and explore the ongoing challenges. Let’s get started.
Understanding the Cloud Network Landscape
The cloud isn’t a physical place; it’s a distributed network of servers. Think of it like renting computing power and storage from a provider. This flexibility brings tremendous advantages, but also unique security concerns.
Unlike traditional on-premises environments, the cloud involves shared infrastructure. This introduces potential vulnerabilities. Your security strategy must account for this shared responsibility model, knowing what your provider handles and what falls on you.
Different cloud deployment models – public, private, and hybrid – also dictate the level of control and security requirements. Each requires a specific security strategy, tailored to its unique attributes.
Ultimately, securing your cloud network requires a shift in mindset. It’s about adapting security practices to a dynamic, distributed environment, rather than simply replicating old methods.
Common Cloud Network Security Threats
Cloud environments face a range of potential dangers. Understanding these threats is the first step toward mitigating them. From data breaches to misconfigurations, the attack surface can be quite extensive.
Data breaches are a primary worry. Cloud storage can hold sensitive data, and attackers are constantly seeking vulnerabilities to exploit. A successful breach can lead to financial losses, reputational damage, and legal repercussions.
Misconfigurations are surprisingly common. Incorrectly configured security settings can unintentionally expose data to the public internet. Automating configuration management can help minimize these risks.
Insider threats, whether malicious or accidental, also pose a challenge. Implementing strong access controls and monitoring user activity can help detect and prevent insider-related incidents.
DDoS attacks can overwhelm cloud resources, disrupting services. A robust network architecture, combined with DDoS mitigation techniques, is vital to ensure business continuity.
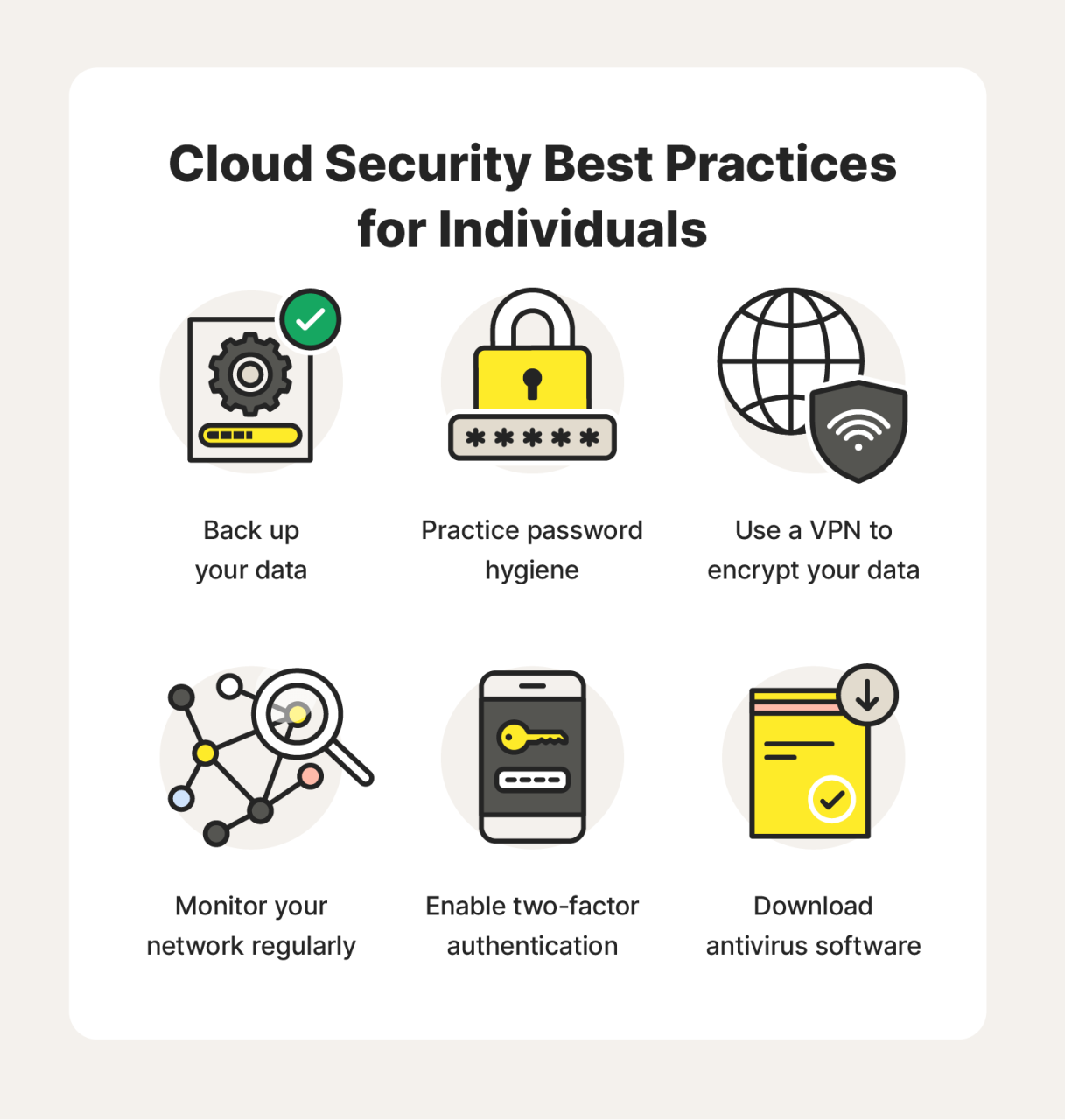
Essential Cloud Network Security Practices
Implementing robust security practices is crucial to protecting your cloud environment. This involves a layered approach, addressing vulnerabilities at multiple levels. Let’s explore some key strategies.
Network segmentation is a foundational principle. Isolating critical resources into separate network segments limits the impact of a breach. Firewalls and virtual networks can enforce these divisions effectively.
Identity and access management (IAM) is vital for controlling who has access to what. Employing multi-factor authentication (MFA) adds an extra layer of security, making it harder for attackers to compromise accounts.
Data encryption protects data at rest and in transit. Encrypting sensitive data makes it unreadable to unauthorized parties, even if they gain access to it.
Regular security audits and vulnerability scanning are essential for identifying and addressing weaknesses. Automating these processes can provide continuous monitoring and alerts.
Incident response planning is also vital. Having a clear plan in place enables rapid response to security incidents, minimizing damage and downtime.
Choosing the Right Security Tools and Technologies
A wide array of security tools and technologies can help you protect your cloud network. Selecting the appropriate solutions depends on your specific needs and environment. Consider these options.
Cloud firewalls provide network-level protection, filtering traffic based on defined rules. They can protect against common network attacks and enforce security policies.
Intrusion detection and prevention systems (IDS/IPS) monitor network traffic for malicious activity. They can automatically block suspicious traffic and alert security personnel.
Security Information and Event Management (SIEM) systems collect and analyze security logs from various sources. This provides a centralized view of security events, aiding in threat detection and incident response.
Cloud workload protection platforms (CWPPs) protect workloads running in the cloud. They offer features like vulnerability scanning, malware detection, and runtime protection.
Cloud security posture management (CSPM) tools help organizations assess and improve their overall cloud security posture. They identify misconfigurations and compliance violations.
The Future of Cloud Network Security
Cloud network security is constantly evolving. New threats emerge regularly, and security technologies continue to advance. Staying ahead of the curve requires ongoing learning and adaptation. So, what does the future hold?
Automation will play an increasingly important role. Automating security tasks reduces human error and speeds up response times. Machine learning can be used to identify and respond to threats automatically.
Zero trust security models are gaining traction. Zero trust assumes that no user or device is trusted by default. All access requests are verified before granting access to resources.
Container security is becoming more important as container adoption grows. Securing container images and runtime environments is crucial to protecting applications.
Serverless security is also a growing concern. Securing serverless functions and applications requires specialized tools and techniques.
The future of cloud network security will likely involve a combination of advanced technologies, automated processes, and a proactive security mindset.