In today’s digital landscape, it’s not a question of if you’ll be targeted by a cyberattack, but when. Organizations are constantly bombarded with phishing scams, ransomware attacks, and sophisticated data breaches. But what if you could anticipate these threats and proactively defend your network? That’s where cyber threat intelligence (CTI) comes in.
CTI is more than just security alerts; it’s about collecting, analyzing, and disseminating information about potential threats to help organizations make informed decisions. By understanding the motives, tactics, and infrastructure of cybercriminals, security teams can move from reactive to proactive, strengthening their defenses and mitigating risks before they materialize.
This article delves into the world of CTI, exploring its core principles, practical applications, and the benefits it offers in navigating the complex and ever-evolving threat landscape. Prepare to learn how to transform threat data into actionable insights and elevate your cybersecurity posture to a new level of resilience.
Cyber Threat Intelligence: Staying Ahead of the Curve
In today’s digital landscape, vigilance is key. Cyber threat intelligence (CTI) provides the insights needed to proactively combat evolving dangers. It’s like having a scout team identifying enemy movements before they reach your doorstep.
CTI leverages data-driven analysis to understand potential threats. This analysis examines their motives, targets, and attack behaviors. The aim is to arm organizations with actionable knowledge.
By understanding the threat landscape, companies can bolster their security posture. They can anticipate attacks, prevent breaches, and minimize the impact of successful intrusions. CTI is no longer a luxury, but a core component of robust security.
Effective CTI involves gathering, processing, and analyzing threat data. The data turns into usable intelligence. This knowledge facilitates well-informed decisions, and enhances overall cybersecurity.
Understanding the Threat Landscape
The cyber threat landscape is constantly shifting, a dynamic battleground. New attack methods emerge daily, while old ones adapt to bypass defenses. Ignoring this reality is to invite risk.
This encompasses malware, phishing campaigns, ransomware, and denial-of-service assaults. It also includes advanced persistent threats (APTs), often orchestrated by sophisticated actors. Awareness of these facets is essential.
Understanding the ‘who,’ ‘what,’ ‘why,’ and ‘how’ of cyber threats paints a vivid picture. Such knowledge offers a strategic advantage in proactive security measures. Knowing the adversaries allows for targeted defense.
Keeping pace requires continuous monitoring and threat data aggregation. Feed analysis is vital to recognize current trends. It is equally important to grasp prospective dangers.
For example, a growing trend of supply chain attacks necessitates careful assessment. This assessment examines third-party vendors and their security practices. Proactive measures reduce risks within the ecosystem.
Sources of Cyber Threat Intelligence
Cyber threat intelligence originates from diverse sources, both internal and external. These sources provide raw data that is then analyzed and refined. This process creates actionable insights.
Sources include: open-source intelligence (OSINT), commercial threat feeds, and government agencies. Information sharing platforms also constitute a rich source of data. Even internal incident reports contribute greatly.
OSINT incorporates news articles, social media, and technical blogs. These provide details about emerging threats and attacker techniques. Commercial feeds provide curated data on known malicious actors.
Collaboration and information exchange are critical. ISACs (Information Sharing and Analysis Centers) facilitate collaboration within specific industries. Sharing intelligence enhances collective security posture.
Leveraging diverse sources is critical for a complete picture. A comprehensive view improves the fidelity of your threat predictions. This completeness results in superior security preparation.
Applying Cyber Threat Intelligence
Effective CTI translates insights into proactive measures. Applying gathered intelligence transforms it from inert data into a powerful defense tool. This is the crucial step of CTI.
CTI guides security investments, informing decisions on technology and staffing. It also aids incident response, enabling faster and more effective containment. Strategic deployment is key.
Use CTI to improve detection rules and alert configurations. It helps to identify suspicious behavior more accurately. Tailor your defenses to address your specific risks based on intelligence.
Further, CTI informs vulnerability management, prioritizing patching based on active exploits. Prioritize patching based on real-world exploits. This helps organizations protect vital assets.
For instance, if CTI indicates a surge in ransomware attacks targeting a specific industry, organizations in that sector can implement heightened security measures. Increased monitoring and employee awareness campaigns will help greatly.
Building a Cyber Threat Intelligence Program
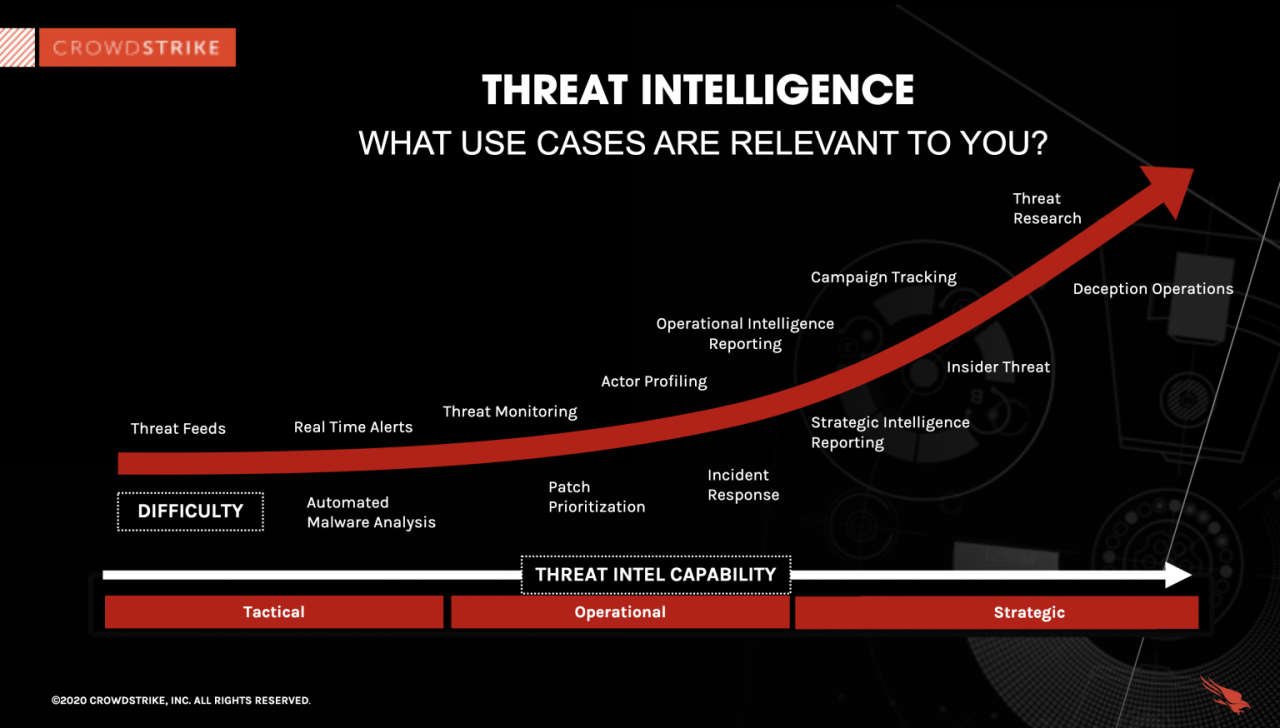
Establishing a CTI program requires planning, resources, and commitment. Build your own CTI program for a sustainable proactive security strategy. This strategy safeguards against evolving threats.
Identify stakeholders, define goals, and secure executive support. Without stakeholder buy-in, your program will face difficulties. A strategic approach ensures program success.
Assemble a team with expertise in security analysis, data science, and threat research. A diverse team brings varied skills and perspectives to the table. Collaboration improves threat detection.
Implement processes for data collection, analysis, and dissemination. Efficient processes ensure that intelligence is actionable and timely. Time is of the essence when dealing with threats.
Regularly evaluate the effectiveness of the CTI program. Refine your processes and ensure continuous improvement. Continuous improvement ensures that it remains relevant and effective. Adapt and update.