In today’s interconnected world, imagine leaving your front door wide open – that’s essentially what happens when your operating system isn’t properly protected. An OS firewall acts as the crucial first line of defense against malicious threats attempting to infiltrate your system.
But what exactly is an OS firewall, and why should you care? It’s the built-in security system within your operating system (like Windows, macOS, or Linux) that monitors and controls incoming and outgoing network traffic, blocking unauthorized access and preventing potential attacks.
This article will demystify OS firewalls, explaining how they work, why they’re essential for protecting your data and privacy, and how to configure them effectively. You’ll learn about common challenges in firewall management and gain practical tips to strengthen your system’s defenses, ensuring a safer and more secure computing experience.
Understanding Your OS Firewall: A Guardian at Your Digital Gate
Think of your operating system firewall like a security guard for your computer. It carefully monitors incoming and outgoing network traffic.
This critical component decides what gets in and what stays out, based on a pre-defined set of rules. It acts as a barrier between your computer and the wider internet.
Without it, your machine would be a sitting duck, vulnerable to all kinds of threats floating around cyberspace. Consider it essential protection.
A properly configured OS firewall is a vital first line of defense against unwanted intrusions. It safeguards your data and privacy from prying eyes.
What Exactly Does an OS Firewall Do?
The primary job of an OS firewall involves carefully examining network packets. These packets are small bundles of data transmitted across the internet.
It meticulously analyzes the origin, destination, and content of each packet. Comparing this info against established rules ensures only safe data passes.
Based on these rules, the firewall either allows the packet to pass or blocks it completely. This process is a core function.
Firewalls protect against unauthorized access, malware infections, and various other network-based dangers. It’s like a bouncer at a nightclub.
Beyond simple blocking, many firewalls also log activity, giving insight into attempted intrusions. This log assists in identifying potential threats.
This information proves valuable for security audits and fine-tuning firewall rules for optimal defense. Understanding these logs is key.
Key Components of a Typical OS Firewall
An OS firewall typically has a few essential parts working together. The rule base is the core, it holds all the instructions.
These rules dictate how the firewall should handle different types of network traffic. They are the backbone of the entire operation.
The filtering engine is what examines the packets and applies the rules. It compares packets against the rule base.
The interface lets you configure the firewall, adding, modifying, or deleting rules. This helps customize your level of security.
Finally, logging is important. It records significant events, letting you analyze security incidents. Good logs are crucial for investigation.
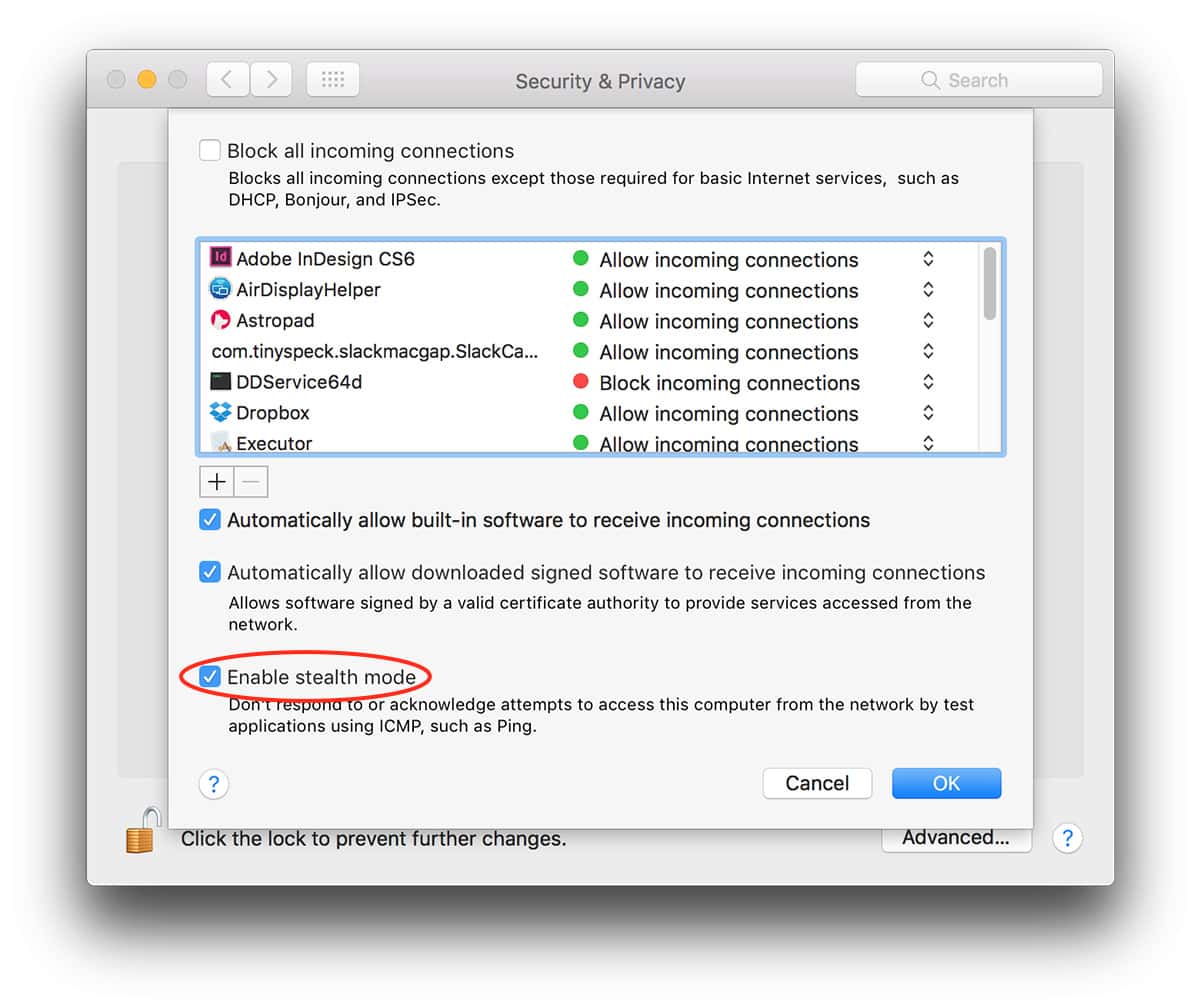
Configuring Your OS Firewall: Basic Steps
Configuring your OS firewall usually starts with accessing its settings through your operating system’s control panel. Find the relevant section first.
From there, you can review existing rules and add new ones to suit your needs. Always back up your settings before any changes.
Pay close attention to the default settings. They should provide decent protection, but they might require some refinement.
Allow only necessary ports and applications through the firewall. Block anything that you don’t recognize or trust for added security.
Regularly update your firewall software to ensure you have the latest security patches and rule definitions. Updates are vitally important.
Consider setting up logging to track any unusual activity or attempted intrusions. Keeping tabs on this information is very important.
Advanced Firewall Techniques and Considerations
Going beyond basic configuration, advanced techniques can boost your firewall’s capabilities. One such method is stateful packet inspection.
This analyzes the context of each packet, not just its header, providing deeper insight. This allows for smarter, more efficient filtering.
Another layer of security is Intrusion Detection Systems (IDS). These look for suspicious patterns in network traffic.
Consider implementing network segmentation to isolate sensitive resources behind the firewall. Segmenting the network adds extra security.
Educate yourself on common attack vectors and vulnerabilities to better understand the risks you’re facing. This allows for proactive security.
Regularly test your firewall’s configuration to verify that it’s working as expected. Run penetration tests occasionally to stay sharp.