In today’s interconnected world, a cyberattack occurs every 39 seconds, leaving businesses vulnerable to significant financial losses and reputational damage. But how can organizations truly understand their vulnerabilities and proactively defend against these ever-evolving threats? The answer lies in cybersecurity risk assessment.
This process is more than just ticking boxes; it’s a critical evaluation of your digital assets, potential threats, and existing security controls. Think of it as a comprehensive health check for your digital infrastructure, identifying weaknesses before they can be exploited.
This article will delve into the core principles of cybersecurity risk assessment, providing you with a practical understanding of how to identify, analyze, and prioritize risks. You’ll learn actionable steps to strengthen your defenses, mitigate potential damages, and build a more resilient security posture, ultimately safeguarding your valuable data and ensuring business continuity.
Cybersecurity Risk Assessment: Protecting Your Digital Assets
In today’s interconnected world, safeguarding your digital information is vital. A cybersecurity risk assessment is like a health check-up for your organization’s data. It helps you identify, analyze, and evaluate potential vulnerabilities.
Think of it as a proactive measure, shielding your business from financial losses, reputational damage, and legal troubles. It’s not just about preventing attacks; it’s about building a resilient security posture.
A robust assessment provides actionable insights. It allows you to prioritize resources, implement effective controls, and improve overall security. It’s a cornerstone of a strong cybersecurity strategy.
Ultimately, this process ensures that your defenses align with the real threats you face. This alignment maximizes security and reduces vulnerabilities that could be costly in the long run.
Why is a Cybersecurity Risk Assessment Important?
Conducting routine assessments can keep you a step ahead of cyber threats. You gain a thorough understanding of your security state. This awareness helps you make knowledgeable judgments.
These assessments highlight weaknesses in your system, offering opportunities for improvement. They also establish a baseline for tracking progress over time. This baseline is critical for continuous improvement.
Beyond technical aspects, these assessments align with compliance requirements. This alignment is crucial for sectors dealing with sensitive data. Proper compliance ensures legal and operational stability.
An assessment builds trust among stakeholders by demonstrating your commitment to data security. Customers, partners, and investors see this as a commitment to protect their valuable information.
Key Components of a Cybersecurity Risk Assessment
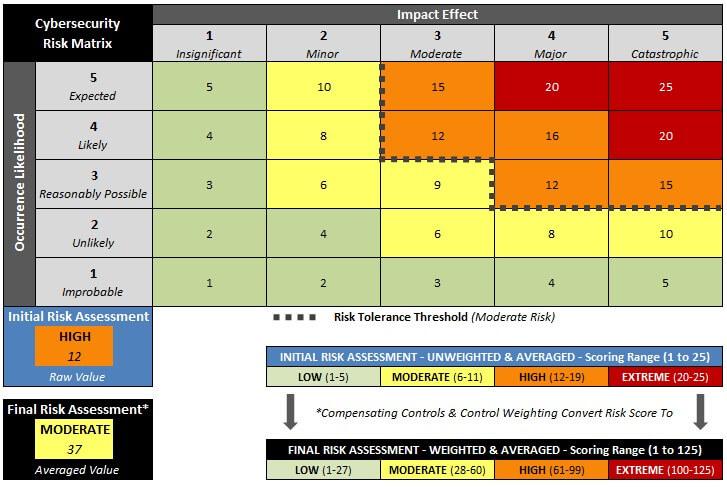
A thorough assessment begins with asset identification. Determine the resources most critical to your operations. This step involves understanding what needs protection.
Next, analyze the potential threats and vulnerabilities that could affect those assets. This analysis requires technical expertise. It helps anticipate possible attack vectors.
Then, evaluate the potential impact of a successful attack. This involves assessing the potential damage to your business. It’s crucial to understand the financial, operational, and reputational risks.
The final stage includes developing an action plan to mitigate identified risks. This plan must prioritize vulnerabilities and guide the implementation of appropriate safeguards.
Steps to Conduct a Cybersecurity Risk Assessment
Start by defining the scope and goals of your assessment. This foundational step ensures that the process addresses the right questions. It provides focus and clarity to the effort.
Next, gather information from diverse sources, like network configurations and security policies. This holistic approach ensures a complete understanding. It reveals hidden vulnerabilities.
Analyze the gathered data to identify potential risks. This requires technical proficiency and a deep understanding of cybersecurity threats. Effective analysis is key for accurate conclusions.
Finally, create a report that outlines the findings and recommends actions. This report should be clear, concise, and actionable. It forms the basis for enhancing your cybersecurity posture.
Tools and Techniques for Cybersecurity Risk Assessments
Vulnerability scanners can automatically identify weaknesses in your systems. These tools expedite the discovery of common misconfigurations. They are essential for efficient threat detection.
Penetration testing simulates real-world attacks to discover vulnerabilities. This hands-on technique assesses the efficacy of existing safeguards. It exposes weaknesses that scanners might miss.
Risk assessment frameworks like NIST or ISO 27001 offer structured methodologies. These frameworks provide a systematic approach for conducting thorough assessments. Compliance and governance are improved.
Utilize threat intelligence feeds for insights into the latest cyber threats. This information helps you stay ahead of evolving risks. Proactive threat intelligence is indispensable.
Best Practices for Cybersecurity Risk Assessments
Regularly update your assessment to address new threats. Cybersecurity is an ongoing battle. Frequent updates keep your defenses effective.
Involve key stakeholders from different departments. A collaborative effort ensures a comprehensive understanding. Diverse perspectives lead to better security.
Prioritize identified risks according to their potential impact. This enables you to focus on the most critical issues. It helps you allocate resources effectively.
Document your assessment process thoroughly for audit and compliance purposes. Clear documentation proves your commitment to security. It simplifies regulatory reviews.
Overcoming Challenges in Cybersecurity Risk Assessments
Limited resources can hinder your assessment efforts. Prioritizing and focusing on critical assets is important. Efficient allocation is crucial when faced with restrictions.
Lack of internal expertise can be addressed by hiring external consultants. They can provide specialized knowledge. External expertise ensures accurate and thorough assessments.
Keeping up with evolving cyber threats can be a challenge. Stay informed through training and participation in industry events. Ongoing education is vital for staying current.
Securing buy-in from management is essential for implementing recommendations. Present the findings with clear business impact. Linking security to business goals ensures adoption.
The Future of Cybersecurity Risk Assessments
AI and machine learning are improving risk assessment processes. They automate threat detection and response. Predictive analytics are becoming more accurate and useful.
Increased automation will enable continuous risk monitoring. Real-time assessments will become more common. This proactive approach improves responsiveness.
Greater integration with cloud security solutions is likely. Protecting data in the cloud is a growing concern. Cloud-native assessments will become essential.
Focus will shift towards a more proactive, threat-informed approach. Understanding emerging threats will be crucial. Predictive risk assessments will be increasingly prevalent.