Imagine a network where security policies are as fluid and responsive as the applications they protect. This is the promise of Software-Defined Networking (SDN), but its centralized control, while offering unprecedented agility, also creates a tempting single point of failure.
SDN security, therefore, isn’t just an add-on; it’s the bedrock upon which the entire SDN architecture must be built. In a world increasingly reliant on interconnected systems and facing ever-evolving cyber threats, securing these networks is paramount.
This article delves into the core challenges of SDN security, exploring the vulnerabilities that arise from its architecture, from compromised controllers to misconfigured policies. We’ll also examine the innovative security mechanisms designed to mitigate these risks, providing you with a practical understanding of how to fortify your SDN deployments and navigate the complex landscape of network security in the age of software-defined infrastructure.
Get ready to unlock the secrets to a secure and resilient SDN environment.
SDN Security: Protecting Your Network’s Future
Software-Defined Networking (SDN) offers incredible flexibility and control. However, this newfound power brings fresh challenges. Securing your SDN infrastructure is paramount to prevent breaches.
SDN’s centralized control plane is both a blessing and a potential vulnerability. A compromise here could bring down the whole network. Let’s explore crucial aspects of securing SDNs.
We’ll unpack the distinctive risks presented by SDN. Plus, we will examine tried-and-true strategies to keep your network safe and performant. Stay one step ahead of attackers.
By understanding SDN security thoroughly, you equip your team to defend against emerging cyber threats. You can proactively safeguard your valuable resources and important data.
Understanding the Unique Security Challenges of SDN
SDNs introduce a distinct architectural shift. This transformation necessitates a revised approach to network protection. Traditional methods may no longer suffice in this brave new environment.
The centralized controller, while empowering, becomes a prime target. If an attacker gains access, they could manipulate network traffic, disable security policies, or even shut down the entire network.
The reliance on APIs and open interfaces also presents security considerations. Vulnerabilities in these interfaces can be exploited to bypass traditional perimeter defenses. Rigorous testing is vital.
Dynamic nature is another layer of intricacy. Constant modifications demand real-time monitoring and adaptive safeguards to maintain a robust security posture throughout the environment.
Furthermore, the decoupling of control and data planes can lead to complex access control scenarios. Policies must be consistently applied and enforced across the distributed network fabric.
Key SDN Security Strategies and Best Practices
Securing an SDN requires a multi-faceted approach. It demands a combination of technology, processes, and expertise. We need to focus on the most effective tactics.
First, enforce strong authentication and authorization for the controller. Multi-factor authentication (MFA) is a must-have to prevent unauthorized access and mitigate the risks of credential theft.
Next, implement robust access control lists (ACLs). These should strictly limit communication between SDN components. This reduces the attack surface significantly. A ‘least privilege’ approach is best.
Employ intrusion detection and prevention systems (IDPS). These provide real-time monitoring of network traffic for suspicious activity. They alert administrators to potential threats.
Regularly audit the SDN controller and network devices for security vulnerabilities. Perform penetration testing to identify weaknesses and validate the effectiveness of security controls.
Segment the network into logical zones. This limits the impact of a breach. Attackers find it tougher to traverse from one segment to another. Isolation is essential for containment.
Utilize encryption to protect data in transit. This prevents eavesdropping and ensures confidentiality. Secure channels should be used for communication among SDN components.
Automate security tasks where possible. This reduces the risk of human error and improves efficiency. Automation also allows for faster response to security incidents. Speed is imperative.
Tools and Technologies for SDN Security
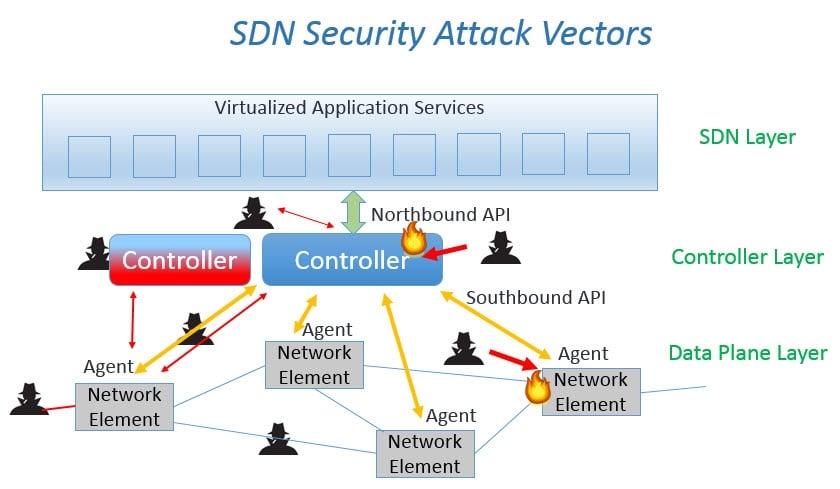
Several tools are available. These enhance the security of SDN deployments. Integrating these correctly ensures an optimal approach for your environment.
Security Information and Event Management (SIEM) systems are important. They provide centralized logging and analysis of security events. Enables proactive threat detection.
Network Behavior Analysis (NBA) tools monitor network traffic patterns. Anomalies can be identified that may signify a security breach. Unusual patterns will be flagged.
SDN firewalls offer granular control over network traffic. They filter malicious content. They enforce security policies based on application, user, and device. This offers fine-grained control.
Threat intelligence feeds provide up-to-date information on emerging threats. This helps you stay ahead of the curve. Enables proactive adaptation of security policies.
Open source security tools like Snort and Suricata can be integrated into SDNs. Provide cost-effective intrusion detection and prevention capabilities. Leverage the power of community.
Future Trends in SDN Security
SDN security is continually evolving. There are new challenges and innovative solutions are being developed. It is essential to remain informed.
Artificial intelligence (AI) and machine learning (ML) are playing an increasing role. They improve threat detection and automated response. Enable faster and more accurate analysis.
Zero-trust security models are gaining traction. These assume that no user or device is inherently trusted. This provides strong authentication and continuous verification.
Cloud-native SDN deployments are becoming more common. This introduces new security considerations. Providers and shared responsibilities must be carefully addressed.
The integration of SDN with other security technologies, such as Security Orchestration, Automation, and Response (SOAR) platforms, is becoming more prevalent.