Imagine a world where factories grind to a halt, power grids flicker and fail, or even water treatment plants malfunction, not because of natural disasters or equipment failure, but due to a cyberattack. This isn’t a scene from a dystopian movie; it’s a real and growing threat facing Operational Technology (OT) systems.
But what exactly is “cyber security OT”? Simply put, it’s the practice of protecting the hardware and software that control critical industrial processes – the very backbone of our infrastructure. Unlike traditional IT systems which manage data, OT systems control physical processes.
Securing these systems is paramount; a breach can have devastating real-world consequences. This article will delve into the unique challenges of securing OT environments, exploring the vulnerabilities that attackers exploit and outlining practical strategies to strengthen your defenses and prevent catastrophic disruptions.
Prepare to uncover the vital steps needed to safeguard the systems that keep our world running.
Cybersecurity for Operational Technology (OT): A Comprehensive Guide
Operational Technology (OT) is crucial. It powers industrial processes and infrastructure. Think factories, power plants, and transportation systems. Securing OT is no longer optional; it’s essential for business continuity and safety.
This isn’t just about firewalls. Protecting OT demands a detailed understanding of its unique challenges and risks. It requires a layered approach.
The convergence of IT and OT networks presents both opportunities and risks. A holistic cybersecurity strategy addresses these converging environments.
Let’s dive into the key aspects of cybersecurity for OT, exploring strategies and best practices. This will help strengthen defenses.
Understanding the OT Landscape
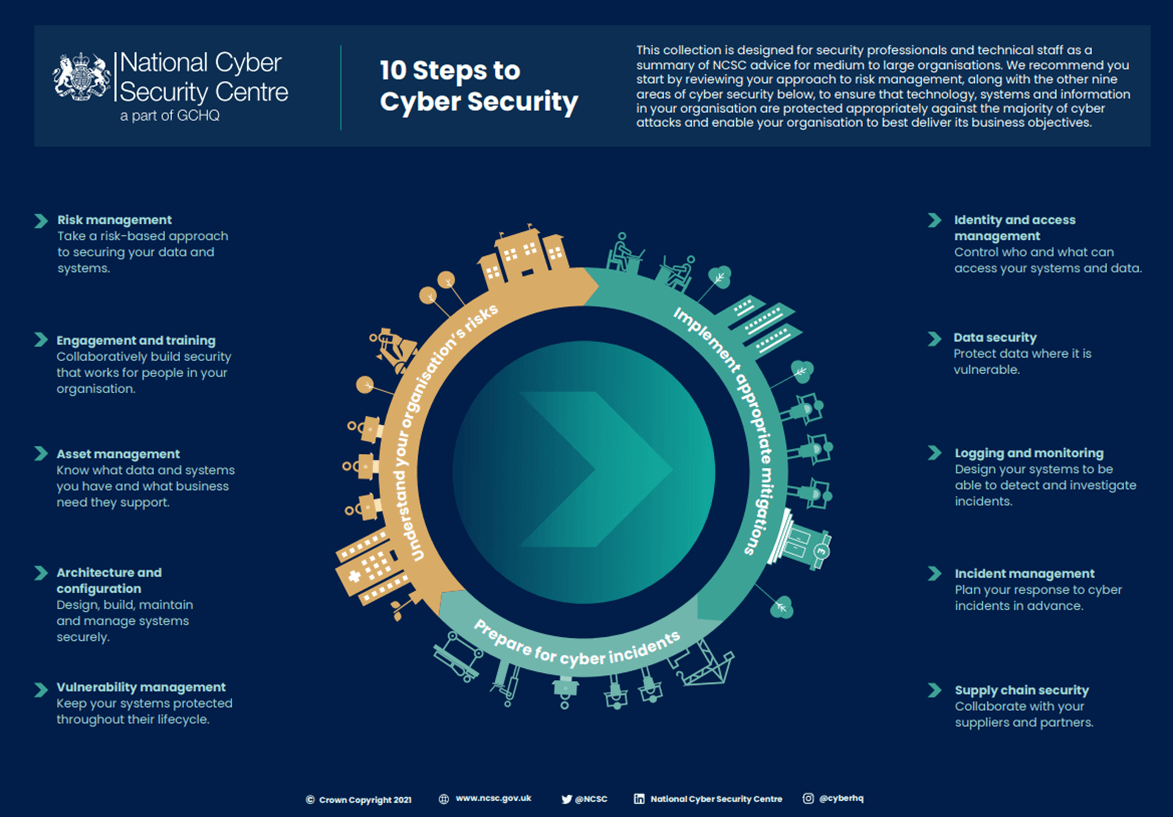
OT systems differ significantly from traditional IT environments. They involve specialized hardware, software, and communication protocols. These assets are often older and lack modern security features.
Unlike IT systems that focus on data, OT prioritizes availability and reliability. Downtime can have severe consequences, ranging from production losses to safety hazards. This influences security decisions.
OT environments often consist of a wide array of devices, including Programmable Logic Controllers (PLCs), Supervisory Control and Data Acquisition (SCADA) systems, and Human-Machine Interfaces (HMIs). Each has its own vulnerabilities.
Many OT networks were originally designed without security in mind, lacking segmentation and robust authentication. This makes them vulnerable to cyberattacks that can disrupt critical operations.
Consider the potential impact on a water treatment facility. A successful attack could alter chemical levels. This would cause a public health crisis. That is why OT security is critical.
Common OT Security Threats and Vulnerabilities
OT environments face many threats, including malware, ransomware, and targeted attacks. These threats can exploit vulnerabilities in OT systems. These can disrupt operations.
Outdated software and firmware represent significant vulnerabilities. Patches are often delayed or unavailable. This leaves systems susceptible to exploits.
Weak authentication and access controls can enable unauthorized access to critical systems. Attackers can compromise accounts. Then they move laterally within the network.
The lack of network segmentation allows threats to spread easily. An infection in one part of the network can quickly impact others.
Insufficient monitoring and logging make it difficult to detect and respond to security incidents. Delays in identifying attacks can increase damage.
Phishing attacks targeting OT personnel are an increasing concern. These campaigns can compromise credentials. Or they can introduce malware into the environment.
Key Strategies for Securing OT Environments
Implementing a layered security approach is essential. This involves multiple security controls that work together to protect critical assets. This is also known as defense-in-depth.
Network segmentation is critical. It isolates critical systems and limits the impact of potential breaches. Use firewalls and VLANs to create secure zones.
Robust identity and access management is essential. Enforce strong passwords, multi-factor authentication, and role-based access control. Limit access based on job function.
Implement regular vulnerability assessments and penetration testing. Identify and remediate weaknesses. Stay ahead of potential threats.
Establish a comprehensive incident response plan. This includes procedures for detecting, containing, and recovering from security incidents. Test the plan regularly.
Enhance monitoring and logging. Gain visibility into OT network activity. Identify anomalous behavior. Respond quickly to potential threats.
Secure remote access channels. Use VPNs and other secure protocols. Ensure that only authorized personnel can access OT systems remotely.
Best Practices for OT Cybersecurity
Develop and enforce clear security policies and procedures. These should address all aspects of OT security. These should be communicated to all personnel.
Provide cybersecurity training to OT staff. Educate them about the latest threats. Teach them about how to recognize and respond to security incidents.
Patch and update OT systems regularly. But, thoroughly test patches. Ensure compatibility before deploying them to production environments.
Implement intrusion detection and prevention systems (IDPS). These can identify and block malicious activity on the OT network. This helps to prevent attacks.
Back up OT systems regularly. Store backups offline. You’ll need this to recover from disasters or cyberattacks. Verify the integrity of backups.
Stay up-to-date on the latest threat intelligence. Monitor security advisories. Understand new vulnerabilities. Take proactive measures to mitigate risks.
The Future of OT Cybersecurity
The future of OT cybersecurity will be shaped by several key trends. These include the increasing adoption of cloud technologies and artificial intelligence (AI).
Cloud-based security solutions offer scalability and cost-effectiveness. They also provide advanced threat detection capabilities. This helps to secure OT environments.
AI-powered security tools can automate threat detection and response. They can also improve the efficiency of security operations. This allows for quicker action.
As OT and IT networks become more integrated, security strategies must adapt. A unified approach to cybersecurity that covers both environments is crucial.
Collaboration between IT and OT teams is essential. Break down silos. Share knowledge. Coordinate security efforts. Protect critical infrastructure.
By embracing these trends, organizations can build more resilient and secure OT environments. This ensures the continued availability and safety of critical operations.