Imagine your network as a bustling city, constantly humming with activity. Now, picture a single security guard trying to monitor every street, every building, and every suspicious character. Overwhelmed, right? That’s where a SIEM network comes in.
SIEM, or Security Information and Event Management, acts as a sophisticated surveillance system, collecting, analyzing, and correlating security data from across your entire IT infrastructure. It’s like having a team of highly trained detectives working 24/7, identifying threats and potential breaches before they cause real damage.
In today’s increasingly complex digital landscape, where cyber threats are constantly evolving, a robust SIEM network isn’t just a luxury; it’s a necessity. In this article, we’ll delve into the intricacies of SIEM networks, exploring their core components, benefits, and how they can help you fortify your organization’s defenses against the ever-present threat of cyberattacks.
Prepare to learn how to transform your security posture from reactive to proactive, ensuring the safety and integrity of your valuable data.
Understanding SIEM Networks: A Comprehensive Guide
SIEM, or Security Information and Event Management, has become a crucial element in modern cybersecurity. It offers a consolidated view of an organization’s security posture. This involves real-time analysis of security alerts generated by various applications and network hardware.
Think of a SIEM network as the central nervous system for your digital defenses. It’s always on, constantly collecting and analyzing data. This data comes from endpoints, servers, network devices, and even cloud services.
SIEM solutions aim to provide a single pane of glass for security teams. This allows them to swiftly detect, analyze, and respond to security threats. Early detection is key to minimizing potential damage.
In essence, a SIEM network helps organizations shift from reactive to proactive security. This means moving beyond merely responding to incidents. Instead, you actively hunt for threats. This proactive approach is vital in today’s complex threat landscape.
What Makes Up a SIEM Network? Key Components
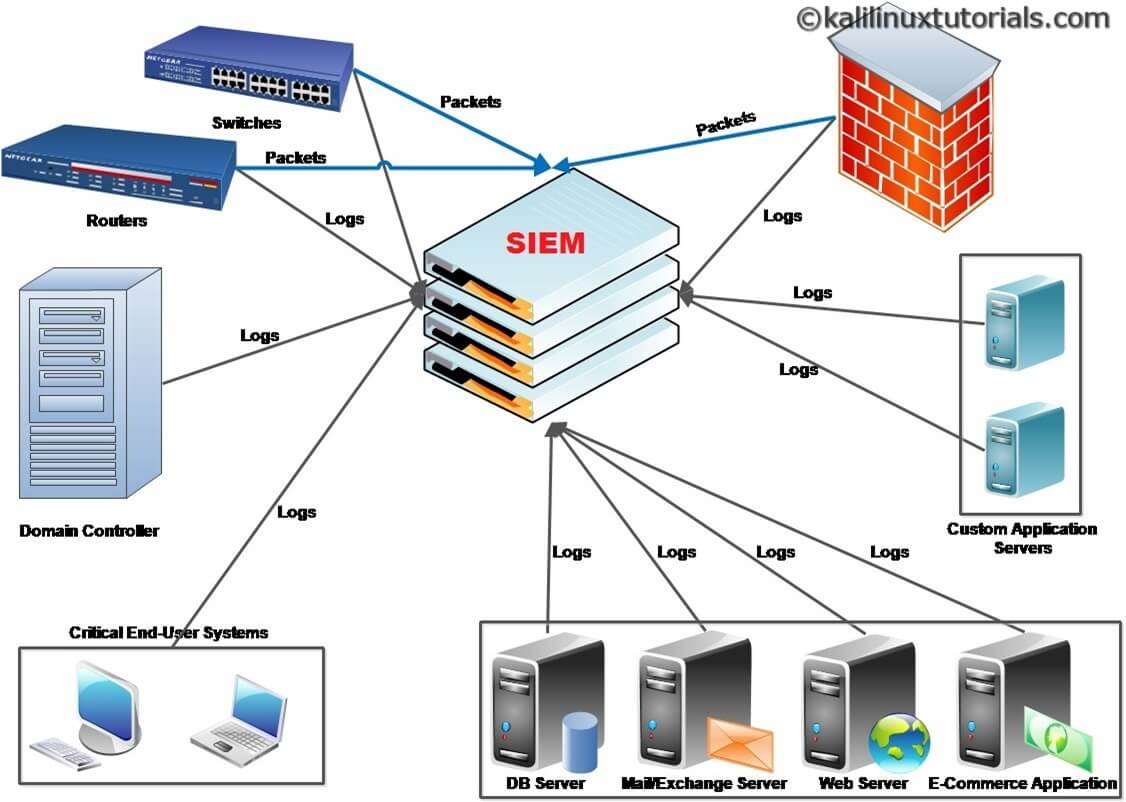
At its core, a SIEM network is composed of several essential components. Log collection is the first step. The system gathers log data from a wide array of sources.
Next comes normalization and aggregation. This process transforms varied log formats into a unified schema. This makes analysis easier.
Correlation is where the magic happens. The SIEM engine analyzes aggregated data to identify patterns. These patterns often reveal suspicious activities or security incidents.
Reporting and alerting are vital for actionable insights. The system generates reports on security trends. It also alerts security teams to critical issues.
Incident management features often come standard. This allows for the tracking and resolution of security incidents. This streamlines the response process and facilitates collaboration.
Benefits of Implementing a SIEM Network
Implementing a SIEM network offers a host of advantages. Improved threat detection is a key benefit. Real-time analysis catches threats that might otherwise go unnoticed.
Enhanced incident response is another crucial aspect. SIEM networks allow for faster identification and containment. This swift action can significantly reduce the impact of breaches.
Compliance is often a driver for SIEM adoption. SIEM systems can assist in meeting regulatory requirements. This includes those established by HIPAA, PCI DSS, and GDPR.
Centralized log management simplifies auditing and forensic investigations. Having all security data in one location streamlines security tasks.
Furthermore, SIEMs provide better visibility into your security posture. You gain a holistic understanding of your environment and its vulnerabilities.
Choosing the Right SIEM Solution: Key Considerations
Selecting the right SIEM solution is a critical decision. Scalability is paramount. Ensure the system can handle your current and future data volume.
Integration capabilities are another vital consideration. The SIEM should easily integrate with your existing security tools. This allows for a more comprehensive security ecosystem.
Ease of use is also important. A user-friendly interface allows your team to leverage the SIEM effectively. Complex or cumbersome systems can hinder efficient incident response.
Consider the vendor’s reputation and support. A reliable vendor provides ongoing support and timely updates. This helps maintain the system’s effectiveness.
Finally, factor in the total cost of ownership (TCO). This includes not only the initial investment but also maintenance and staffing costs. A clear understanding of the TCO helps with budget planning.
The Future of SIEM Networks: Emerging Trends
The SIEM landscape is constantly evolving. One emerging trend is the integration of User and Entity Behavior Analytics (UEBA). This helps to identify anomalous behaviors that could indicate insider threats or compromised accounts.
Another trend is the adoption of Security Orchestration, Automation, and Response (SOAR). SOAR allows for automated incident response workflows. This drastically reduces response times.
Cloud-based SIEM solutions are also gaining popularity. They offer scalability and reduced infrastructure management.
Artificial Intelligence (AI) and Machine Learning (ML) are playing an increasingly important role. These technologies help to improve threat detection accuracy and reduce false positives.
The convergence of SIEM with other security tools is also on the rise. This leads to more comprehensive and integrated security solutions.