Imagine a digital fortress: robust walls, sophisticated surveillance, and vigilant guards at every entry point. That’s essentially what checkpoint network security aims to be. In today’s hyper-connected world, where cyber threats are constantly evolving and becoming increasingly sophisticated, securing your network isn’t just good practice – it’s a necessity for survival.
Checkpoint network security provides a comprehensive approach to protecting your digital assets by implementing a series of security controls at strategic points within your network. But what exactly does that entail? And how do you ensure these checkpoints are truly effective against the ever-growing threat landscape? This article will delve into the core components of checkpoint network security, exploring the technologies, strategies, and best practices needed to build a strong and resilient defense against cyberattacks.
Get ready to discover how to fortify your network and safeguard your valuable data.
Understanding Checkpoint Network Security
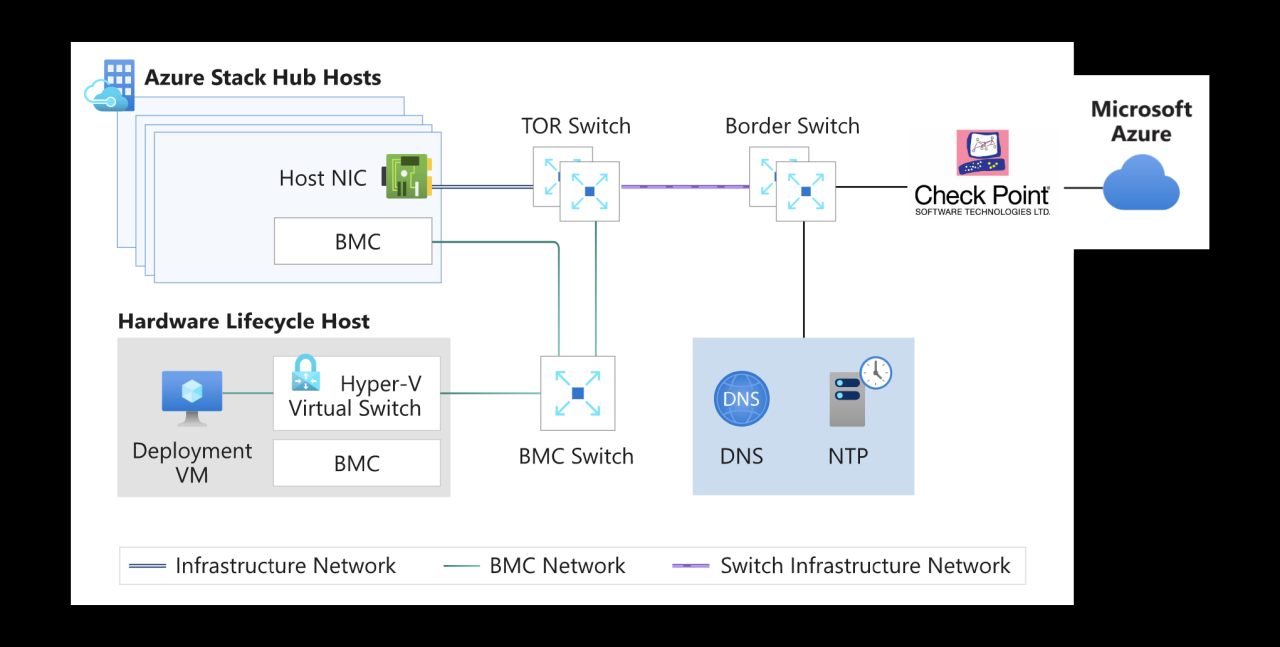
Let’s dive into the world of Checkpoint network security. It’s a big player, offering a broad suite of tools to safeguard your digital assets. Think of it as a comprehensive security umbrella, shielding your network from cyber threats.
Checkpoint focuses on proactive protection. Their tech aims to identify and neutralize dangers before they can cause havoc. This approach is vital in today’s landscape where attacks are constantly evolving.
Essentially, Checkpoint offers solutions ranging from firewalls to threat prevention. It’s a layered defense strategy designed to keep your data safe and your operations running smoothly. The goal is resilience against a wide array of threats.
Beyond the products, Checkpoint also emphasizes threat intelligence. They gather and analyze data to stay ahead of emerging risks. This proactive approach is key to maintaining robust security.
Key Components of Checkpoint’s Security Suite
At the heart of Checkpoint’s offerings is their firewall. This is the initial line of defense, inspecting traffic and blocking unauthorized access. It’s a foundational element of network security.
Beyond the basic firewall, Checkpoint provides intrusion prevention systems (IPS). These go deeper, analyzing traffic for malicious activity. This helps to catch sophisticated attacks that bypass basic firewalls.
Another vital component is their advanced threat prevention. This includes sandboxing, anti-bot, and anti-virus capabilities. These technologies work together to identify and neutralize malware.
Secure access solutions are also critical. Checkpoint offers VPNs and other tools to ensure secure remote access to your network. This is particularly important with the rise of remote work.
Finally, Checkpoint provides endpoint security. This protects individual devices, such as laptops and smartphones, from threats. This adds a crucial layer of security outside the main network perimeter.
Benefits of Using Checkpoint Solutions
One major benefit is enhanced security posture. Checkpoint provides a comprehensive, integrated approach to threat prevention. It minimizes the risk of successful cyberattacks.
Improved compliance is another advantage. Checkpoint solutions can help you meet industry regulations and standards. This reduces the risk of penalties and legal issues.
Centralized management is also key. Checkpoint’s management platform allows you to monitor and control your security infrastructure from a single location. This simplifies security administration.
Reduced operational costs can be a significant benefit. By automating security tasks and preventing breaches, Checkpoint can save you time and money. A proactive defense approach is more cost-effective in the long run.
Furthermore, Checkpoint can improve network performance. Their solutions are designed to minimize latency and avoid hindering legitimate traffic. You get security without sacrificing speed.
Deployment Options and Considerations
Checkpoint offers flexibility in deployment. You can choose on-premises appliances, cloud-based solutions, or a hybrid approach. This allows you to tailor the solution to your specific needs.
Consider your network infrastructure. The best deployment option will depend on the size, complexity, and location of your network. Assess your needs carefully before making a decision.
Scalability is another important factor. Choose a solution that can grow with your business. This will ensure that your security can keep pace with your evolving needs.
Don’t forget about integration. Ensure that Checkpoint solutions integrate with your existing security tools and systems. Seamless integration simplifies management and improves overall security.
Proper training is crucial. Ensure that your IT staff is trained to manage and maintain the Checkpoint solution. This will maximize the effectiveness of your security investment.
Real-World Applications of Checkpoint Network Security
Financial institutions rely on Checkpoint to protect sensitive data. They need robust security to prevent fraud and maintain customer trust. This is paramount in the banking sector.
Healthcare organizations use Checkpoint to comply with HIPAA regulations. They need to safeguard patient data and prevent breaches. Protecting medical records is a legal requirement.
Government agencies deploy Checkpoint to protect critical infrastructure. They need to defend against cyberattacks and maintain national security. These networks are under constant attack.
Retail businesses use Checkpoint to protect customer payment information. They need to prevent data breaches and maintain PCI compliance. Customer trust is vital for online sales.
Educational institutions use Checkpoint to protect student data and network resources. They need to create a safe and secure online learning environment. This supports a positive learning experience.