In today’s interconnected world, a single cyberattack or data breach can cripple an organization, leading to significant financial losses and irreparable reputational damage. Are you truly confident that your incident response plan can handle the ever-evolving threat landscape? IBM Resilient, now part of IBM Security QRadar SOAR, offers a powerful solution to orchestrate and automate your security incident response, helping you to not only react effectively but also proactively manage potential crises.
This article delves into the core functionalities of IBM Resilient, exploring how it streamlines workflows, reduces response times, and empowers security teams to collaborate seamlessly. We’ll uncover its key features, benefits, and how it can transform your organization’s ability to navigate the complexities of modern cybersecurity, ensuring a more secure and resilient future.
Understanding IBM Resilient: Your Guide to Incident Response
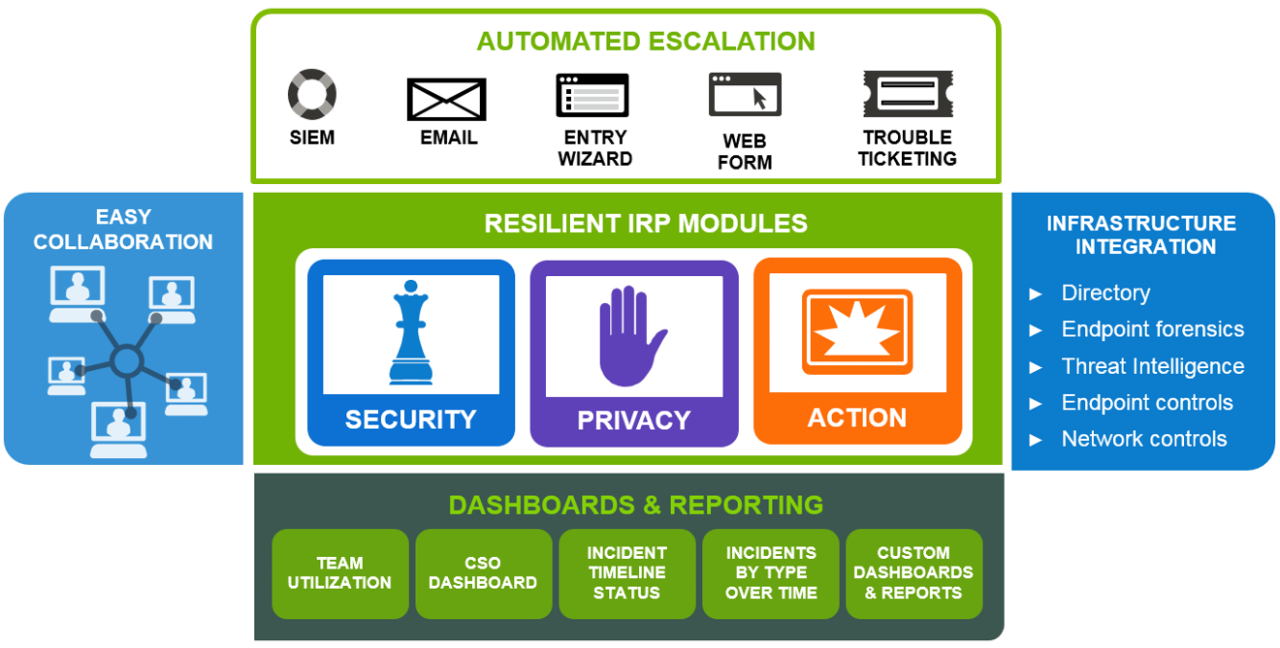
IBM Resilient, now known as IBM Security QRadar SOAR, is a comprehensive security orchestration, automation, and response (SOAR) platform. It empowers security teams to streamline incident response, reduce response times, and improve overall security posture.
Think of it as your central command center for handling security incidents. It brings together all the necessary tools, workflows, and intelligence to manage incidents effectively from detection to resolution.
By automating repetitive tasks and providing a structured approach to incident handling, IBM Resilient allows security analysts to focus on more complex and critical issues, enhancing their productivity and efficiency.
Ultimately, it translates into a stronger defense against cyber threats and reduced business impact from security breaches. It’s about being proactive, not reactive, when it comes to cybersecurity.
Key Features and Benefits of IBM Resilient
At the heart of IBM Resilient lies its powerful automation engine. This capability automates manual tasks such as data enrichment, containment actions, and reporting, freeing up valuable time for security personnel. This leads to faster incident resolution and a more effective security team.
The platform offers customized playbooks that align with your organization’s specific security policies and procedures. This ensures that incidents are handled consistently and in accordance with best practices. You can also build playbooks from scratch or use pre-built ones.
IBM Resilient integrates seamlessly with a wide range of security tools and threat intelligence feeds. This provides security teams with a holistic view of the threat landscape and enables them to make more informed decisions. It fosters a comprehensive security ecosystem.
It offers detailed reporting and analytics capabilities. These provide valuable insights into incident trends, response effectiveness, and areas for improvement. You can identify vulnerabilities and take proactive steps to mitigate future risks. Data is key here.
Benefits stretch beyond automation. Improved communication and collaboration among security teams are key components. Better consistency in incident handling and a reduced risk of human error also make a noticeable difference.
How IBM Resilient Works: A Simplified Overview
The platform begins with incident detection. When a security event occurs, such as a malware alert or a suspicious login, it is automatically ingested into IBM Resilient. This acts as a trigger point for initiating the incident response process.
Then, the platform enriches the incident data with relevant information from various sources. This includes threat intelligence feeds, vulnerability scanners, and log management systems, providing context and insights into the nature of the threat. Having this contextual data is crucial.
Based on the incident type and severity, a pre-defined playbook is automatically initiated. The playbook guides the security team through the necessary steps to investigate, contain, and eradicate the threat. It also ensures a structured approach to incident response.
Throughout the incident response process, IBM Resilient automates various tasks. These range from isolating affected systems to blocking malicious IP addresses, freeing up security analysts to focus on more complex aspects of the investigation. This allows for a swift and effective resolution.
Once the incident is resolved, the platform generates detailed reports. These reports document the entire incident response process, including the actions taken, the time to resolution, and the lessons learned. This provides valuable insights for future incident handling.
Use Cases for IBM Resilient Across Industries
Within the financial sector, IBM Resilient helps organizations respond to fraudulent transactions, data breaches, and other security incidents that can impact customer trust and regulatory compliance. Quick and consistent responses are vital.
In healthcare, the platform assists in handling incidents involving patient data breaches, ransomware attacks, and medical device vulnerabilities. Protecting patient privacy and ensuring the availability of critical healthcare services are paramount.
For retailers, IBM Resilient helps mitigate risks associated with point-of-sale (POS) intrusions, e-commerce fraud, and supply chain disruptions. Maintaining a secure and reliable retail environment is essential for business continuity.
Manufacturing firms leverage IBM Resilient to safeguard their intellectual property, prevent cyber espionage, and respond to industrial control system (ICS) incidents. Protecting critical infrastructure and proprietary information is crucial.
Government agencies utilize IBM Resilient to defend against cyberattacks targeting critical infrastructure, sensitive data, and national security interests. Maintaining a strong and resilient defense posture is paramount.
Getting Started with IBM Resilient: Implementation Tips
Start by defining your specific incident response goals and objectives. What are the key areas you want to improve? What metrics will you use to measure success? Align Resilient with your overall security strategy and address immediate needs.
Clear goals set the stage.
Identify the key security tools and threat intelligence feeds that you want to integrate with IBM Resilient. This will enable you to automate data enrichment and correlation, providing a more comprehensive view of the threat landscape.
Integration is critical for a holistic view.
Develop customized playbooks that align with your organization’s unique security policies and procedures. Start with simple playbooks and gradually expand to more complex scenarios. Continuous refinement is critical for optimal performance.
Provide comprehensive training to your security team on how to use IBM Resilient effectively. This will ensure that they are able to leverage the platform’s full capabilities and respond to incidents efficiently. Empowering your team leads to maximum effectiveness.
Monitor the performance of IBM Resilient and make adjustments as needed. Continuously evaluate your playbooks, integrations, and workflows to ensure that they are optimized for your environment. Adaptation is key to long-term success.