In today’s digital landscape, can any organization truly afford to leave its digital defenses to chance? The answer, undoubtedly, is no. Cybersecurity threats are constantly evolving, and businesses of all sizes are under relentless attack. But fortifying your infrastructure doesn’t always require a hefty investment in proprietary software.
Enter cybersecurity open source tools: a powerful and often overlooked arsenal of freely available software designed to detect, prevent, and respond to cyber threats. This isn’t just about saving money; it’s about access to innovative solutions, community-driven development, and unprecedented customization.
This article will delve into the world of these tools, exploring their capabilities, highlighting some of the best options available, and providing you with the knowledge to leverage open source to strengthen your security posture. Prepare to discover how you can harness the power of open collaboration to defend against the ever-growing cyber threat landscape.
Unlocking Security: Your Guide to Open Source Cybersecurity Tools
In today’s digital world, staying secure is paramount. Luckily, you don’t need a huge budget to get solid protection. The open source community offers a treasure trove of cybersecurity tools, and many are free!
These tools are built by developers, security experts, and everyday users sharing knowledge and expertise. That results in adaptable, constantly evolving solutions capable of tackling a wide array of digital risks.
This article aims to explore some of the amazing open source cybersecurity tools that can help protect your network, data, and devices. We’ll look at different areas, from spotting threats to securing web applications.
Whether you’re a seasoned IT professional or just getting started, there’s something here for everyone. So, dive in and learn about the power of community-driven security!
Network Security Powerhouses
Your network is the backbone of your digital life, and needs robust protection. A bunch of free tools can help fortify your perimeter and detect suspicious activity.
Suricata is a powerful intrusion detection and prevention system (IDS/IPS). This tool analyzes network traffic in real time. It scans for suspicious patterns, malicious code, and policy violations.
Suricata’s strength lies in its ability to use existing detection rule sets, making it easy to adapt to your specific security needs. It’s like having a vigilant guard constantly watching for intruders.
Snort is an older, more mature IDS/IPS system. This offers similar protection as Suricata, relying on rules and signatures to find threats. It’s a solid choice for anyone already familiar with its ecosystem.
Nmap (Network Mapper) is a utility for network exploration or security auditing. It’s used for discovering hosts and services on a computer network by sending packets and analyzing the responses. Nmap is highly adaptable and can discover system and service info.
OpenVAS is a comprehensive vulnerability scanner. It scans your network for known weaknesses and gives detailed reports to help you patch them before attackers find them. It’s great for maintaining a proactive security posture.
Web Application Security Guardians
Web applications are often prime targets for attacks. Protecting them is vital for your overall security. There are some quality open source solutions available.
OWASP ZAP (Zed Attack Proxy) is a free, easy-to-use penetration testing tool for finding vulnerabilities in web apps. It’s actively maintained and a fantastic tool to have in your toolbox.
ZAP acts as a “man-in-the-middle” proxy, letting you intercept and examine web traffic to identify potential flaws. It’s useful for both developers and security professionals.
Nikto is a popular web server scanner that performs comprehensive tests against web servers. It checks for dangerous files, outdated server software, and other potentially exploitable vulnerabilities.
Nikto is a straightforward scanner that helps to identify common misconfigurations and weaknesses. Regular scans with Nikto can help you stay ahead of potential threats.
W3af is a web application attack and audit framework. This tool can automatically find and exploit vulnerabilities in web applications. It’s an invaluable tool for security experts conducting thorough assessments.
Endpoint Protection: Securing Your Devices
Your computers and devices are the front lines of your digital defense. Robust endpoint protection is essential. There are free choices here as well.
ClamAV is a well-known open source antivirus engine. It can detect trojans, viruses, malware, and other malicious threats. It works for Windows, Linux, and macOS.
ClamAV is a dependable solution that offers real-time scanning capabilities. It is updated regularly with the latest threat definitions.
OSSEC is a host-based intrusion detection system (HIDS). It monitors your systems for suspicious activity and policy violations.
OSSEC provides log analysis, file integrity monitoring, rootkit detection, and real-time alerting. It gives a comprehensive view of your system’s security posture.
Lynis is a security auditing tool for systems running Linux, macOS, or Unix-based operating systems. It performs deep scans to check system security arrangements.
Lynis can identify potential vulnerabilities and gives suggestions to improve your system’s security. It’s a valuable tool for compliance assessments.
Security Information and Event Management (SIEM)
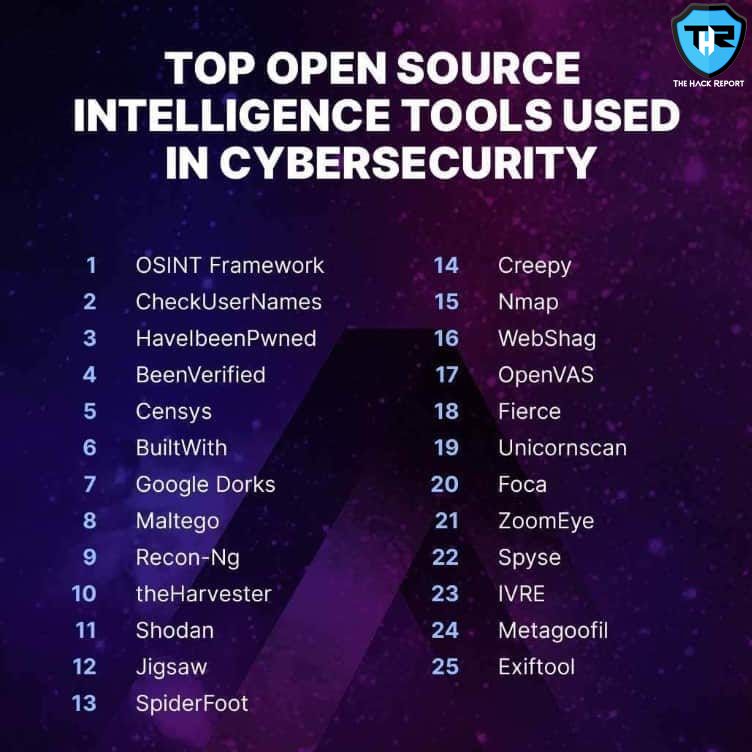
SIEM solutions consolidate security information from multiple sources. They help analyze this data to detect and respond to incidents. There are open source options that can do a great job.
Security Onion is a free and open source Linux distribution for threat hunting, enterprise security monitoring, and log management. It comes packed with tools like Suricata, Snort, Zeek (formerly Bro), and Elasticsearch.
Security Onion provides a unified platform for collecting, analyzing, and visualizing security data. It helps you to quickly identify and respond to threats.
Wazuh is an open source security monitoring solution. It provides capabilities like intrusion detection, log analysis, file integrity monitoring, and vulnerability detection.
Wazuh can be deployed on-premise or in the cloud. It can integrate with other security tools. This makes it a versatile option for businesses of all sizes.
Choosing the Right Tools: Some Considerations
The best tools for you will depend on your specific needs, skills, and resources. Here are some things to think about.
Consider your technical abilities. Some tools are easier to use than others. Start with something simple if you’re new to cybersecurity.
Assess your specific security risks. Understand what you need to protect and find tools that address those specific threats.
Think about your budget and resources. While the tools themselves are free, you’ll still need to spend time and money setting them up and maintaining them.
Don’t be afraid to experiment. Try out different tools and see what works best for you. The open source community is there to help you.
Conclusion
Open source cybersecurity tools offer a wide range of capabilities to protect your digital assets. They empower individuals and organizations to improve their security posture without huge investments.
By exploring these tools and understanding their uses, you can construct a robust security defense system. This helps you mitigate risks and safeguard your data.
Embrace the open source community and start using these solutions today. Take the first step toward a more secure digital future.
Remember that the field of cybersecurity is constantly evolving. Stay updated on the latest threats and tools. Continue to improve your security skills.