Imagine your home alarm blaring in the dead of night. Do you fumble for the off switch, or do you have a plan, a process, to assess the threat and react accordingly? In the digital world, a cyber security incident is that blaring alarm, signaling a potential breach or attack.
Incident response in cyber security is essentially your plan of action – a structured and systematic approach to identify, contain, eradicate, and recover from security incidents. It’s not just about fixing the immediate problem; it’s about minimizing damage, preventing future occurrences, and restoring normal operations as quickly as possible.
This article delves into the crucial elements of a robust incident response plan, exploring best practices, common challenges, and the critical steps needed to protect your organization from the ever-evolving threat landscape. Learn how a well-defined incident response strategy can transform a potential disaster into a manageable event, ultimately strengthening your overall security posture and safeguarding your valuable assets.
Incident Response in Cybersecurity: A Comprehensive Guide
Cybersecurity incidents are, unfortunately, a fact of life in today’s digital landscape. It’s not a question of if you’ll experience one, but when. That’s why having a robust incident response plan is absolutely vital.
This guide will break down the core components of incident response, equipping you with the knowledge to build and execute a plan that minimizes damage and gets you back on track swiftly.
We’ll cover everything from identification and containment to eradication and recovery, offering practical tips and best practices along the way. Think of it as your roadmap for navigating the turbulent waters of a cyberattack.
Ultimately, effective incident response is about being prepared, remaining calm under pressure, and acting decisively. Let’s dive in and get you ready.
What is Incident Response?
Incident response is more than just reacting to a problem; it’s a structured approach to handling cybersecurity incidents. It’s a pre-defined, step-by-step process designed to limit the impact of an attack.
Think of it like a fire drill. You don’t wait for a real fire to figure out what to do. You practice the steps in advance, so everyone knows their role and can react quickly and efficiently when the alarm sounds.
A well-crafted incident response plan will outline roles and responsibilities, communication protocols, and technical procedures. This helps ensure a coordinated and effective response.
The goal is to minimize damage, restore normal operations as quickly as possible, and prevent similar incidents from happening again. This proactive approach can save you time, money, and reputational damage.
It’s about getting your team to work together to identify, investigate, contain, and then recover from an attack, but also learning from the event in order to improve in the future.
Why is Incident Response Important?
Ignoring incident response is like driving without insurance. You might be okay for a while, but when something goes wrong, the consequences can be devastating. A quick, defined reaction can prevent major fall out from a cyber attack.
A swift and effective response can limit the scope of the attack, preventing it from spreading to other systems or data. This reduces the potential damage and cost associated with the incident.
Incident response helps you comply with regulations and avoid hefty fines. Many industries have specific requirements for data security and incident reporting.
It safeguards your reputation. How you handle a security breach can significantly impact your brand image and customer trust. A transparent and responsible response can help maintain confidence.
Think of it like this: you want to show customers that you are taking their data security very seriously, and by having a plan you are doing just that.
Finally, effective incident response provides valuable insights for improving your overall security posture. By analyzing past incidents, you can identify vulnerabilities and strengthen your defenses.
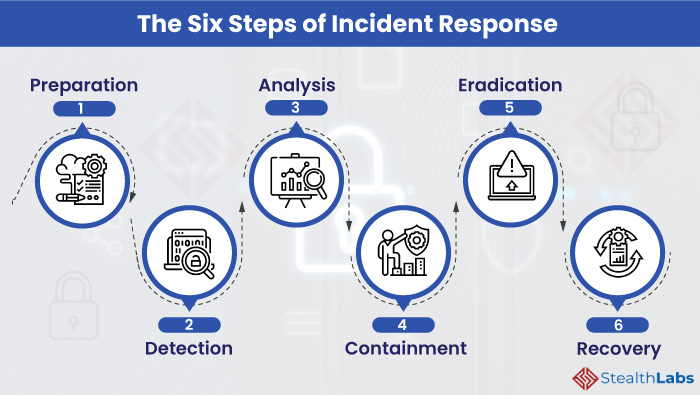
The Incident Response Lifecycle
The incident response lifecycle is a framework that outlines the key stages involved in handling a security incident. While variations exist, a common model includes six phases:
- Preparation: This involves establishing policies, procedures, and tools needed for incident response. This is about training personnel, setting up communication channels, and documenting everything.
- Identification: This phase focuses on detecting and analyzing potential security incidents.
This might involve monitoring logs, analyzing network traffic, and investigating user reports.
- Containment: The goal here is to limit the scope and impact of the incident. This could involve isolating affected systems, disabling compromised accounts, and blocking malicious traffic.
- Eradication: This phase involves removing the root cause of the incident.
This might include patching vulnerabilities, removing malware, and restoring systems from backups.
- Recovery: This involves restoring affected systems and data to normal operations. This could include verifying system integrity, monitoring for further incidents, and communicating with stakeholders.
- Lessons Learned: This final phase involves documenting the incident, analyzing what happened, and identifying areas for improvement.
The idea is to learn from mistakes and strengthen your security posture.
Understanding each phase is crucial for developing an effective and comprehensive incident response plan. Each of these steps should be thoroughly documented.
Building Your Incident Response Plan
Creating a solid incident response plan doesn’t have to be overwhelming. Start by assessing your current security posture and identifying your most critical assets. Knowing what to protect is half the battle.
Define clear roles and responsibilities for your incident response team. Who is in charge of communication? Who handles technical analysis? Clear ownership is essential.
Establish communication protocols for internal and external stakeholders. How will you notify employees, customers, and regulatory agencies? Transparency is key.
Develop detailed procedures for each phase of the incident response lifecycle. Provide step-by-step instructions for common scenarios. The more specific, the better.
Regularly test and update your plan. Conduct simulations and tabletop exercises to identify weaknesses and ensure everyone is prepared. Practice makes perfect.
Document your plan clearly and make it accessible to the entire incident response team. A well-documented plan is much more likely to be used correctly in a crisis.
Key Tools and Technologies
A variety of tools and technologies can support your incident response efforts. These can range from simple utilities to sophisticated security solutions.
Security Information and Event Management (SIEM) systems aggregate and analyze logs from various sources to detect suspicious activity. These are essential for early incident identification.
Endpoint Detection and Response (EDR) solutions monitor endpoints for malicious behavior and provide tools for containment and remediation. They can help stop attacks in their tracks.
Network traffic analysis tools provide visibility into network activity and can help identify malicious traffic patterns. This is invaluable for understanding the scope of an attack.
Vulnerability scanners identify weaknesses in your systems and applications, allowing you to proactively address them. Prevention is always better than cure.
Finally, consider using threat intelligence feeds to stay informed about the latest threats and vulnerabilities. Knowledge is power in the fight against cybercrime.