Imagine your digital life – your personal photos, banking information, and crucial work documents – suddenly exposed and vulnerable. That’s the chilling reality of cyber threats today. With online attacks becoming increasingly sophisticated and frequent, relying solely on firewalls and antivirus software is no longer enough.
This is where intrusion prevention software (IPS) steps in. But with a market flooded with options, how do you choose the best IPS to safeguard your valuable data? An effective IPS acts as a vigilant guard, proactively identifying and blocking malicious activity before it can cause damage.
In this article, we’ll cut through the noise and explore the top contenders in the IPS landscape, highlighting their key features, strengths, and weaknesses. You’ll gain the knowledge needed to make an informed decision and choose the intrusion prevention software that best fits your specific needs and protects your digital world from ever-evolving threats.
Best Intrusion Prevention Software: Shielding Your Network
In today’s digital landscape, safeguarding your network is paramount. Intrusion Prevention Systems (IPS) act as vigilant sentinels, proactively identifying and neutralizing malicious activities before they inflict harm.
Think of it as your network’s immune system, constantly scanning for anomalies and taking swift action to thwart potential breaches. Selecting the appropriate IPS solution can dramatically enhance your security posture.
This comprehensive guide navigates the complex world of intrusion prevention software, helping you make an informed decision to protect your valuable data and maintain seamless operations. We’ll explore top contenders and their critical features.
Choosing the best IPS is a crucial step in building a robust cybersecurity defense. It’s about finding a solution that aligns with your specific needs and infrastructure.
Understanding Intrusion Prevention Systems
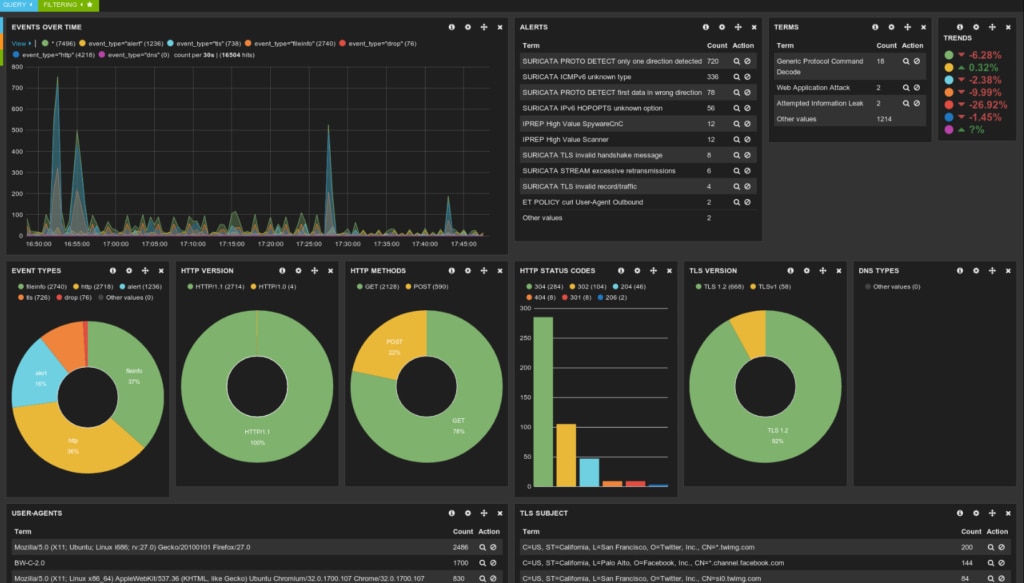
An IPS functions by closely examining network traffic for suspicious patterns indicative of cyberattacks. These systems use various methods, from signature-based detection to behavior analysis, to pinpoint threats.
Unlike Intrusion Detection Systems (IDS), which simply alert you to potential issues, IPS actively blocks or mitigates these threats in real-time. This proactive approach is vital in minimizing damage and preventing further infiltration.
Think of an IDS as a security camera alerting you to a possible intruder, while an IPS is the security guard who intercepts the intruder before they can cause any harm. The IPS is more involved, actively trying to stop the event.
IPS solutions often include features like packet analysis, protocol analysis, and heuristic analysis. These techniques combined provide a multi-layered defense against evolving cyber threats.
The aim of IPS is to stop the attack before it becomes harmful and causes significant disruptions or data loss. The importance of an IPS in network security should not be taken for granted.
Key Features to Look For
When evaluating intrusion prevention software, certain features stand out as crucial differentiators. Real-time threat detection is paramount, enabling immediate responses to emerging attacks.
Customizable rules and policies allow you to tailor the IPS to your specific network environment and security requirements. This ensures that the system accurately identifies and addresses threats relevant to your organization.
Consider the reporting and analytics capabilities of the IPS. Detailed logs and insightful reports are essential for understanding security incidents and improving your overall security posture. Integration is also important.
Automated response capabilities are also a plus. The ability of the IPS to automatically quarantine infected devices or block malicious traffic saves time and resources, reducing the impact of a security breach.
Support for various deployment options is vital. Choose a solution that can be deployed effectively within your infrastructure, whether on-premises, in the cloud, or in a hybrid environment.
Top Intrusion Prevention Software Options
Several leading vendors offer robust intrusion prevention solutions, each with its own strengths and weaknesses. Cisco offers a comprehensive security suite with integrated IPS capabilities, known for its enterprise-grade performance.
Another popular choice is McAfee, providing a wide range of security solutions, including a powerful IPS that integrates seamlessly with its other offerings. They have been industry leaders for many years.
For organizations prioritizing cloud security, Palo Alto Networks offers a next-generation firewall with advanced threat prevention features, specifically designed for cloud environments. They are highly regarded.
Trend Micro provides comprehensive security solutions, including IPS, focusing on protecting against advanced threats like ransomware and targeted attacks. Their solutions are known to be effective.
Finally, Fortinet offers a range of network security appliances with integrated IPS, known for their high performance and scalability, suitable for large enterprises. Their systems are highly favored.
Deployment Considerations
Before deploying intrusion prevention software, it’s essential to carefully assess your network architecture and security requirements. Consider factors such as network bandwidth, traffic volume, and the sensitivity of your data.
Proper configuration is crucial to ensure the IPS effectively identifies and blocks threats without disrupting legitimate traffic. Regular updates and maintenance are vital to keep the system up-to-date with the latest threat signatures.
A phased rollout may be beneficial, allowing you to gradually introduce the IPS into your network and monitor its performance. This approach minimizes the risk of unexpected disruptions and allows you to fine-tune the configuration.
It’s also important to educate your IT staff about the IPS and its capabilities. Proper training ensures they can effectively manage the system and respond to security incidents appropriately. Consider investing in staff training.
Regular testing and vulnerability scanning are essential to ensure the IPS is functioning correctly and that your network remains secure against evolving threats. These are important components of maintaining a resilient security posture.
The Future of Intrusion Prevention
The field of intrusion prevention is constantly evolving, driven by the increasing sophistication of cyberattacks. Machine learning and artificial intelligence are playing an increasingly important role in threat detection and response.
Cloud-based IPS solutions are gaining popularity, offering scalability, flexibility, and cost-effectiveness. As organizations migrate to the cloud, these solutions provide essential security for their cloud workloads.
Integration with other security tools, such as SIEM (Security Information and Event Management) systems, is becoming increasingly common, providing a more holistic view of the security landscape.
Zero-trust security models are also influencing the evolution of IPS, emphasizing the need for continuous authentication and authorization, even within the network perimeter. These models represent a significant shift in security thinking.
The future of intrusion prevention lies in proactive threat hunting, intelligent automation, and seamless integration with other security technologies. Remaining adaptable and aware of emerging trends is key to maintaining robust security.