In today’s digital landscape, where data breaches are a constant threat and users expect seamless access, securing your applications and data is more critical than ever. But how do you balance robust security with a user-friendly experience? Enter IBM Security Verify Access, a powerful solution designed to simplify identity and access management (IAM).
Think of it as the gatekeeper to your digital kingdom, ensuring only authorized individuals gain entry while keeping malicious actors at bay. This article will delve into the core capabilities of IBM Security Verify Access, exploring how it empowers organizations to streamline authentication, enhance security posture, and ultimately, deliver a better user experience.
We’ll unpack its key features, discuss real-world applications, and highlight how it can help you navigate the complexities of modern identity management, paving the way for a more secure and efficient future.
IBM Security Verify Access: Your Key to Modern Access Management
In today’s complex digital landscape, securing access to your applications and data is paramount. IBM Security Verify Access offers a robust and adaptable solution, simplifying identity management and bolstering your overall security posture.
It is designed to handle the ever-evolving needs of modern businesses. This encompasses everything from cloud applications to on-premises systems, all while ensuring a seamless user experience.
Think of it as the gatekeeper to your digital kingdom. It ensures that only those with the right credentials gain entry, protecting your sensitive assets from unauthorized access.
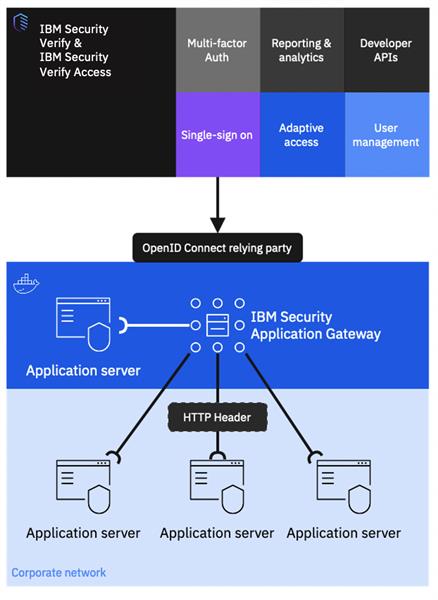
This solution is more than just a password manager; it is a comprehensive identity and access management (IAM) platform built for the demands of today’s sophisticated threats and user expectations.
Understanding the Core Components of Verify Access
IBM Security Verify Access is a modular platform, which comprises several key components that work in harmony. It helps ensure secure, compliant, and user-friendly access control.
Central to its functionality is the Access Management component. This is what dictates who can access what, enforcing policies and controlling user access permissions.
Then, we have Advanced Access Control. It provides context-based access decisions. This adds a layer of smart security that adapts to the changing environment and user behavior.
Federation is key. Verify Access allows you to establish secure connections between different identity providers and applications, enabling single sign-on (SSO) and simplified access across organizational boundaries.
Finally, API Protection safeguards your APIs. These act as doorways to data and functionality, controlling access and preventing misuse. It protects them from unauthorized access and malicious attacks.
Key Benefits of Implementing IBM Security Verify Access
Choosing IBM Security Verify Access can significantly enhance your security posture. It offers a variety of benefits that extend beyond simple access control, improving efficiency and reducing risk.
Improved Security is a primary advantage. By centralizing access management and enforcing strong authentication policies, it minimizes the risk of unauthorized access and data breaches.
Enhanced User Experience is another key benefit. Users gain convenient single sign-on (SSO) access to multiple applications, eliminating the need to remember numerous usernames and passwords.
Streamlined Compliance is essential in today’s regulatory environment. Verify Access helps you meet industry and regulatory requirements. These requirements include GDPR and HIPAA, with comprehensive audit trails and reporting capabilities.
Reduced IT Costs can be achieved by automating access management tasks. This reduces administrative overhead and improving overall efficiency. It helps you free up resources to focus on other critical tasks.
Use Cases: Where Verify Access Shines
The versatility of IBM Security Verify Access allows for diverse use cases across various industries and organizational sizes. It is a great option for handling access challenges of all scales.
For example, imagine a large enterprise with thousands of employees needing access to numerous applications. Verify Access simplifies access management. It provides a single sign-on (SSO) experience, reducing login fatigue and boosting productivity.
Consider a financial institution needing to secure sensitive customer data. It enables multi-factor authentication (MFA) and advanced access controls. It ensures that only authorized personnel can access confidential information, preventing fraud and data breaches.
Or a healthcare provider who wants to comply with HIPAA regulations. It can implement role-based access control and comprehensive audit trails. This ensures the security and privacy of patient data while meeting stringent compliance requirements.
Getting Started with IBM Security Verify Access
Implementing IBM Security Verify Access involves careful planning and execution. Luckily, IBM provides robust support to guide you through the process and ensure a successful deployment.
Begin by defining your access management requirements. Identify the applications, users, and resources that need to be protected. This will help you tailor your Verify Access implementation to your specific needs.
Explore the various deployment options. These options include on-premises, cloud-based, and hybrid environments. Choose the model that best aligns with your infrastructure and business requirements.
Leverage IBM’s expertise. Engage with IBM’s consultants and support teams to gain guidance and assistance throughout the implementation process. Their knowledge can prove invaluable.
Continually monitor and optimize your Verify Access deployment. Regularly review access policies and user activity to ensure ongoing security and compliance. This is an on-going activity to adapt to your evolving needs.