In today’s relentlessly evolving threat landscape, where a new cyberattack erupts seemingly every second, can your organization truly afford to gamble on outdated security measures? The harsh reality is that traditional antivirus software is often a step behind, leaving gaping vulnerabilities exploitable by sophisticated malware.
Enter Cisco Advanced Malware Protection (AMP), a comprehensive security solution designed to combat the most persistent and evasive threats. Think of it as your organization’s advanced early warning system, continuously analyzing files, networks, and endpoints to detect, block, and remediate malware before it can inflict serious damage.
This article will delve into the core capabilities of Cisco AMP, explaining how its unique blend of preventative, detective, and response-oriented features provides unparalleled protection. We’ll explore its real-time threat intelligence, sandboxing capabilities, and powerful endpoint detection and response (EDR) features, arming you with the knowledge to understand how Cisco AMP can fortify your defenses and keep your data safe from the ever-present threat of advanced malware.
Cisco Advanced Malware Protection: A Deep Dive
Staying ahead of evolving digital perils requires robust cybersecurity. Cisco Advanced Malware Protection (AMP) stands out. It is an endpoint security solution designed for this very purpose.
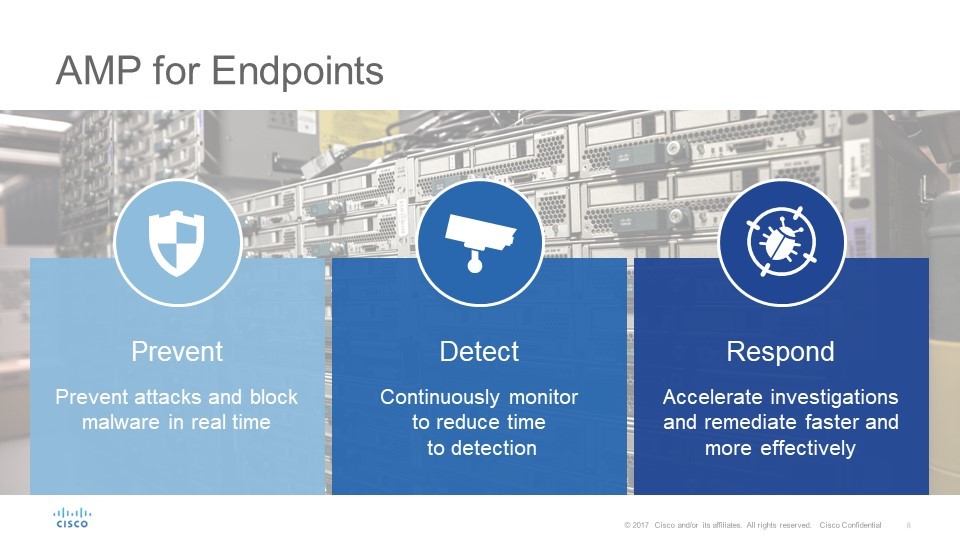
Think of AMP as a vigilant watchdog guarding your digital perimeters. It doesn’t just react to threats; it proactively seeks them out. This approach is what sets it apart.
It’s more than just a firewall; AMP digs deep, monitoring file behavior. It also analyzes data patterns across your entire network. This provides a comprehensive defense strategy.
Understanding Cisco AMP is crucial for any organization serious about shielding its assets. Let’s break down its key features and benefits.
Understanding the Core Components of Cisco AMP
At its foundation, Cisco AMP is built around a few vital elements. These components cooperate to provide robust threat protection. Consider them as the gears within a clock.
The Threat Grid sandbox is a key component, enabling safe detonation of suspicious files. This lets you see the impact of threats without risking your live systems.
Another crucial element is the AMP Connector. This light agent installs on endpoints, gathering data. It transmits it back to the AMP cloud for advanced analysis.
Finally, the AMP portal gives administrators a centralized view. It allows them to manage policies, investigate incidents, and respond to threats effectively.
These parts working together deliver a powerful defense mechanism. The end result is a secure, resilient network.
Key Features and Benefits of Cisco AMP
Cisco AMP has various capabilities that offer tangible value. These functions are designed to enhance security and reduce risk. It streamlines your security processes too.
Continuous analysis and retrospective security are vital. Even after a file is deemed safe, AMP monitors its behavior. If something changes, AMP reacts.
Cloud-based intelligence provides up-to-date threat information. Cisco’s Talos security intelligence helps AMP stay ahead of the newest risks.
Integration is key. AMP integrates with other Cisco security products. This creates a layered and unified security posture.
Reduced time to detection and response are significant. AMP helps security teams quickly identify and neutralize threats. This minimizes potential harm.
How Cisco AMP Works: A Simplified Explanation
Imagine a detective solving a mystery. Cisco AMP works similarly. It gathers clues, analyzes them, and then takes action. Let’s walk through the procedure.
First, the AMP Connector gathers data from your endpoints. It monitors files, processes, and network activity for odd behaviors.
Next, this data is sent to the AMP cloud. Here, advanced analytics and machine learning algorithms are applied. They look for patterns and anomalies.
If a threat is detected, AMP takes immediate action. This might involve blocking a file or isolating an infected endpoint.
Retrospective security constantly monitors files, even after initial analysis. If the reputation of a file changes, AMP can remediate.
Deployment Options for Cisco AMP
Cisco AMP offers versatile deployment choices. This allows businesses to tailor the solution to their specific needs. This makes it adaptable to various circumstances.
Cloud-managed deployment is the simplest to implement. All management and analysis are performed in the cloud. It’s great for smaller organizations.
On-premises deployment provides maximum control. Organizations with stringent security policies can host the system themselves.
A hybrid approach combines both cloud and on-premises aspects. This allows organizations to balance convenience with control. This offers flexibility in approach.
Consider your organization’s scale, resources, and security requirements when choosing a model. It helps you maximize the benefits.
Integrating Cisco AMP with Other Security Solutions
Standalone security tools can only do so much. Integrating AMP with your security ecosystem unlocks greater protection. Think of it as a puzzle.
AMP integrates with Cisco’s firewalls like the Next-Generation Firewall. This provides protection at the network edge. That prevents dangers from entering at all.
It also integrates with email security solutions. This helps protect against phishing and malware distributed via email. This is a common attack vector.
AMP’s integration with SIEM systems boosts threat visibility. It enhances incident response. It provides a single pane of glass view.
By consolidating your security tools, you make your security team more efficient. You can also protect your organization better.