In today’s digital landscape, it’s a sobering fact: a cyberattack occurs every 39 seconds. This constant barrage highlights the critical importance of application and network security, the invisible shield protecting our data and digital infrastructure. But what exactly does that entail? Simply put, it’s the layered approach to safeguarding applications and networks from unauthorized access, use, disclosure, disruption, modification, or destruction.
Think of it as the complex system of locks, alarms, and security guards surrounding your most valuable assets online. This article will delve into the core principles of application and network security, exploring common vulnerabilities, effective defense strategies, and best practices you can implement to bolster your defenses.
By understanding the threats and adopting proactive security measures, you can significantly reduce your risk and ensure a safer, more secure digital experience. Let’s unlock the secrets to safeguarding your online world.
Application and Network Security: A Deep Dive
Understanding the Landscape
The digital world is brimming with opportunity, but it’s also a battleground. Threats lurk around every corner, seeking to exploit weaknesses. We need to understand the environment to secure it properly.
Application and network security are two crucial pillars. Protecting your data, systems, and users requires vigilance. Failing to do so can have devastating consequences.
Network security safeguards the infrastructure. This encompasses firewalls, intrusion detection, and prevention systems. They control network access and monitor traffic.
Application security focuses on the software itself. This means finding and fixing vulnerabilities during development. It also means protecting against runtime attacks.
Both are vital to a strong overall security posture. They work in tandem to provide layered protection. It’s not an either/or situation, but a collaborative effort.
Staying informed about emerging threats is key. Cybersecurity is a constant arms race. What worked yesterday might not work today.
Common Application Vulnerabilities
Applications are often the weakest link. They interact with external systems and handle sensitive information. This makes them prime targets for attackers.
SQL injection remains a persistent threat. Attackers inject malicious code into database queries. This allows them to bypass authentication or steal data.
Cross-site scripting (XSS) exploits trust. Attackers inject malicious scripts into websites. These scripts can steal user credentials or redirect users to fake sites.
Broken authentication is another frequent issue. Weak passwords, lack of multi-factor authentication, leave doors open. These are easily exploitable.
Insecure direct object references expose internal data. Attackers manipulate URLs to access resources. They should not have permission to access.
Understanding these vulnerabilities is paramount. Developers must write secure code. Security teams must regularly scan for vulnerabilities.
Key Network Security Measures
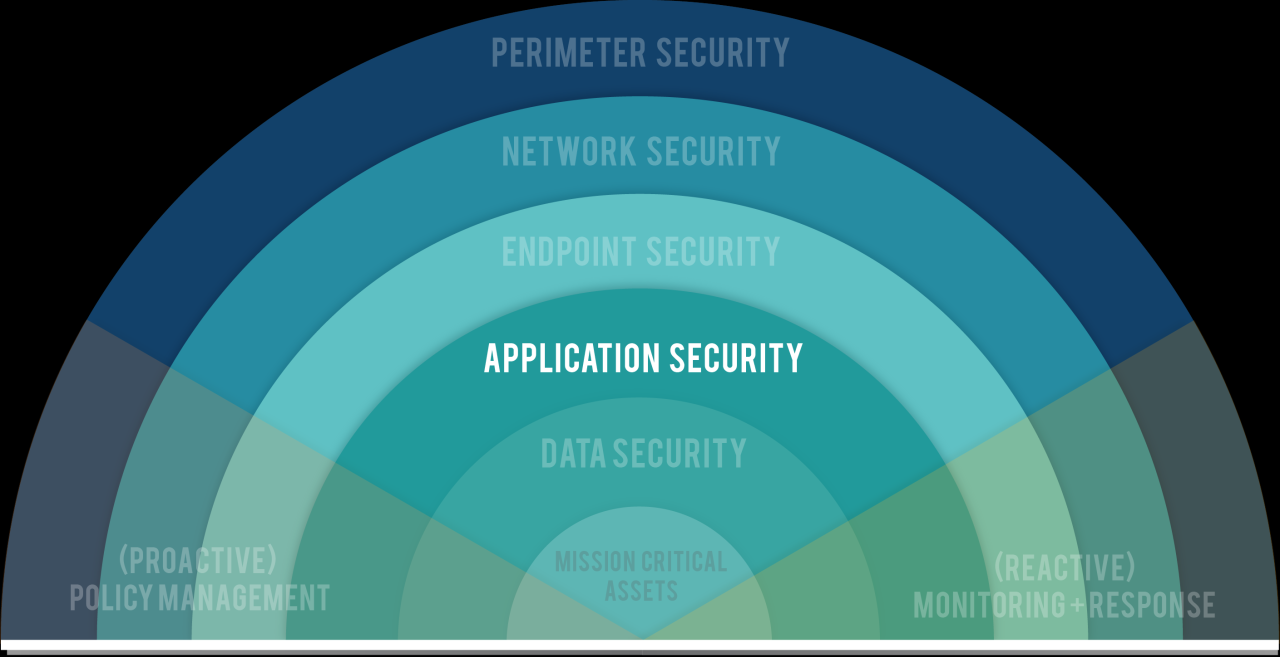
Network security is all about controlling access. It is about monitoring traffic, and preventing unauthorized activity. Think of it as guarding the gates to your digital kingdom.
Firewalls are a fundamental component. They act as barriers between networks. They filter traffic based on pre-defined rules.
Intrusion detection systems (IDS) monitor network traffic. They look for suspicious patterns and anomalies. They alert administrators to potential attacks.
Virtual Private Networks (VPNs) provide secure connections. They encrypt traffic between devices and networks. This is crucial for remote access.
Network segmentation divides the network into smaller zones. This limits the impact of a breach. If one segment is compromised, others remain protected.
Regular security audits and vulnerability assessments are crucial. They identify weaknesses and ensure security controls are effective.
Best Practices for Secure Development
Secure development starts early in the software lifecycle. “Shift left” security. This means integrating security practices from the beginning.
Implement secure coding standards. This can help developers avoid common pitfalls. These pitfalls are the root cause of many vulnerabilities.
Perform regular code reviews. Peer review can catch errors and vulnerabilities. It can also share knowledge among team members.
Use static analysis tools. They automatically scan code for vulnerabilities. This is before it’s even deployed.
Conduct penetration testing. Simulate real-world attacks. Identify weaknesses and validate security controls.
Educate developers on security best practices. This makes them active participants in security. It’s not just the security team’s responsibility.
The Future of Application and Network Security
The security landscape is constantly evolving. New technologies and threats emerge every day. Staying ahead requires innovation and adaptation.
Artificial intelligence (AI) is playing an increasingly important role. AI can automate threat detection and response. It can also improve vulnerability analysis.
Cloud security is a major area of focus. As organizations migrate to the cloud, new security challenges arise. It requires new approaches.
Zero trust security is gaining traction. This model assumes that no user or device is inherently trustworthy. It requires strict authentication and authorization.
Automation is key to scaling security efforts. It’s hard to keep up with the volume of threats. Automated tools can help prioritize and respond.
Continuous monitoring and incident response are essential. Detect and respond to threats. Minimize damage and ensure business continuity.