In today’s interconnected world, where data breaches are increasingly common, how secure is your digital fortress? For anyone running a Linux operating system, the built-in firewall is your first and often strongest line of defense.
But simply having a firewall isn’t enough; understanding how to configure and manage it effectively is crucial. This article dives deep into the world of Linux OS firewalls, explaining what they are, why they are essential for protecting your system from unauthorized access, and, most importantly, how to use them effectively.
We’ll explore popular tools like `iptables` and `firewalld`, demystifying their complexities and providing practical examples to help you fortify your Linux environment. Prepare to gain the knowledge you need to confidently secure your system and keep unwanted intruders at bay.
Linux OS Firewall: Your System’s First Line of Defense
Securing your Linux system is paramount in today’s digital landscape. A robust firewall acts as a gatekeeper, regulating network traffic and shielding your system from unauthorized access and potential threats. Think of it as a digital bodyguard, constantly vigilant.
Linux offers powerful and flexible firewall solutions built right into the kernel. These tools, like iptables and its more user-friendly successor, nftables, provide granular control over network traffic, making them indispensable for any Linux user.
This article explores the world of Linux firewalls. We will cover basic principles, configuration options, and best practices to help you fortify your system’s security. A well-configured firewall significantly reduces your risk profile.
Understanding the ins and outs of a Linux firewall empowers you to manage your network security proactively. This guide aims to demystify the process and equip you with the knowledge to create a secure environment.
Understanding Firewall Basics
A firewall operates by inspecting network packets entering and leaving your system. Each packet is examined against a set of rules, determining whether it should be allowed (accepted) or blocked (dropped). This process forms the core of firewall functionality.
These rules are defined based on various criteria, including the source and destination IP addresses, port numbers, and the protocol used (e.g., TCP, UDP). This level of detail allows you to create highly specific security policies.
Flexibility is key here.
Firewalls often use the concept of chains to organize rules. Packets traverse these chains, being evaluated by each rule in sequence. The first rule that matches dictates the action taken – accept or reject. Consider it a security checklist.
Default policies are essential. A default deny policy blocks all traffic unless explicitly allowed. Conversely, a default allow policy allows all traffic unless explicitly blocked. The former is generally preferred for security. Less is often more.
Stateful firewalls are more advanced. They keep track of active connections, allowing return traffic for established connections without requiring explicit rules. This simplifies rule management and enhances security. This is a significant advantage.
Choosing the Right Firewall Tool: iptables vs. nftables
iptables has been a staple in Linux firewalls for many years. It’s a command-line utility that allows you to manage the kernel’s netfilter framework. While powerful, its syntax can be complex and challenging to learn.
nftables is the modern replacement for iptables. It boasts a more streamlined syntax, improved performance, and enhanced flexibility. It’s designed to be easier to use and more efficient than its predecessor. It’s the evolution of firewalls.
While iptables still enjoys widespread use, nftables is gradually becoming the default choice in many distributions. Its improved syntax and performance make it a compelling alternative for both novice and experienced users alike.
The underlying netfilter framework remains the same for both. They are just interfaces. The significant distinction resides in how you interact with and manage the firewall rules. Choose what works best for you.
Migrating from iptables to nftables requires some learning, but the benefits often outweigh the initial effort. Consider exploring nftables if you’re new to Linux firewalls or looking to upgrade your security setup. It is often worth the investment.
Configuring Your Firewall: Essential Rules and Policies
Start by defining your basic security goals. What services need to be accessible from the outside? What traffic should be strictly prohibited? This clarity guides your firewall configuration.
Implement a default deny policy. This ensures that all traffic is blocked unless explicitly allowed. It’s a fundamental principle of good security practice. Think of it as closing all doors by default.
Allow established and related connections. This permits return traffic for connections initiated from your system, as well as related protocols like FTP data connections. Essential for normal network function.
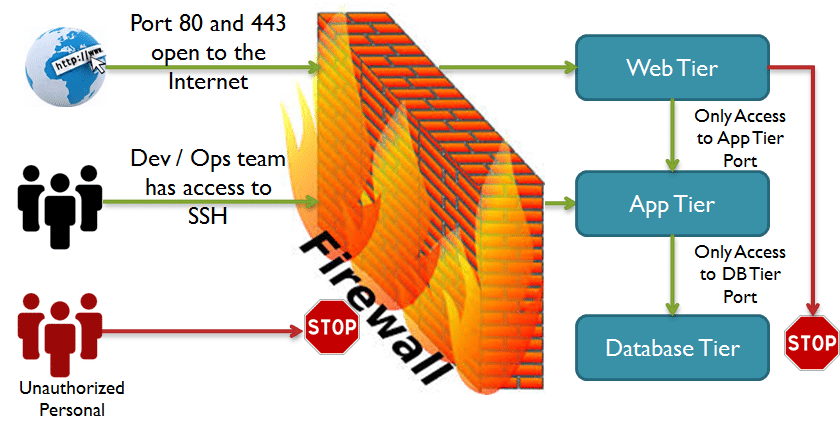
Open only the necessary ports for services you want to expose. For example, allow port 80 (HTTP) and 443 (HTTPS) for a web server. Limiting exposure reduces potential attack vectors.
Log dropped packets. This provides valuable insights into potential attacks or misconfigurations. Regularly review the logs to identify and address security issues. Knowledge is power when dealing with threats.
Practical Examples: Allowing SSH and Web Traffic
To allow SSH access (port 22), use the following nftables command: nft add rule inet filter input tcp dport 22 accept. This permits incoming TCP traffic on port 22. Security requires precise specifications.
To allow HTTP (port 80) and HTTPS (port 443) traffic, use these nftables commands: nft add rule inet filter input tcp dport 80 accept and nft add rule inet filter input tcp dport 443 accept. Essential for web server functionality.
Remember to save your firewall rules after making changes. Otherwise, they will be lost upon reboot. Use the appropriate command for your distribution, such as nft list ruleset > /etc/nftables.conf and systemctl enable nftables.service to ensure persistence.
These examples illustrate how to create specific rules to control network traffic. Adapt these commands to your particular needs and security requirements. Customization is crucial for tailored security.
Always test your firewall configuration thoroughly after making changes. Ensure that your intended services are accessible and that unwanted traffic is blocked. Verification is vital to a functional firewall.
Best Practices for Linux Firewall Management
Regularly review your firewall rules. As your network needs evolve, your firewall configuration should be updated accordingly. Security is an ongoing process.
Use descriptive comments for your rules. This makes it easier to understand the purpose of each rule and simplifies troubleshooting. Clarity is key in complex configurations.
Implement rate limiting to protect against denial-of-service (DoS) attacks. This prevents malicious actors from overwhelming your system with excessive traffic. This limits the impact of attacks.
Stay informed about the latest security threats and vulnerabilities. Keep your firewall software up-to-date with the latest patches and security updates. Proactive defense is the best approach.
Consider using a firewall management tool to simplify configuration and monitoring. Several graphical interfaces and command-line utilities are available to streamline the process. Consider them for easier management.