In today’s digital landscape, could your business survive a cyber attack? The truth is, many organizations are unknowingly vulnerable, leaving their data, finances, and reputation at risk. A cyber security audit is more than just a technical assessment; it’s a crucial health check for your digital defenses.
It’s a comprehensive examination of your systems, policies, and procedures designed to identify weaknesses before they’re exploited. This isn’t about scaremongering; it’s about proactive protection. In this article, we’ll delve into the intricacies of cyber security audits, revealing what they entail, why they are essential, and how conducting one can fortify your business against evolving cyber threats.
Prepare to learn how to transform your security posture from reactive to resilient.
Cyber Security Audit: Protecting Your Digital Assets
In today’s digital landscape, a robust cyber security posture isn’t just desirable; it’s a necessity. A cyber security audit acts as a health check for your organization’s defenses, identifying vulnerabilities and providing a roadmap for improvement.
Think of it as a comprehensive security assessment. These checks delve deep into your systems, policies, and procedures to expose potential weaknesses before malicious actors do.
This proactive approach ensures that your sensitive data remains secure, your operations remain uninterrupted, and your reputation remains intact. Let’s delve into the world of cybersecurity audits and how they can fortify your digital fortress.
Ignoring this vital step can have devastating consequences, ranging from financial losses and reputational damage to legal repercussions and business disruptions. Protect your assets, understand your vulnerabilities, and build a stronger defense through a cyber security audit.
Why is a Cyber Security Audit Important?
A key benefit is identifying areas where your cyber security measures fall short. The audit pinpoints the weaknesses that can be exploited by attackers, offering a clear picture of your risk profile.
These audits help demonstrate compliance with industry regulations and legal requirements, such as GDPR, HIPAA, and PCI DSS. Maintaining compliance not only avoids hefty fines but also builds trust with customers and partners.
By assessing your existing security controls, an audit ensures that your investments are effective and aligned with your business needs. This optimizes your resources, allowing you to prioritize spending on the most critical areas.
Ultimately, a cyber security audit reduces the likelihood and impact of cyber security incidents. This minimizes the potential for financial losses, reputational damage, and operational disruptions, keeping your business running smoothly.
Regular audits empower your team with the insights needed to continuously improve your security posture. This proactive approach keeps you ahead of emerging threats and ensures long-term protection.
Key Elements of a Cyber Security Audit
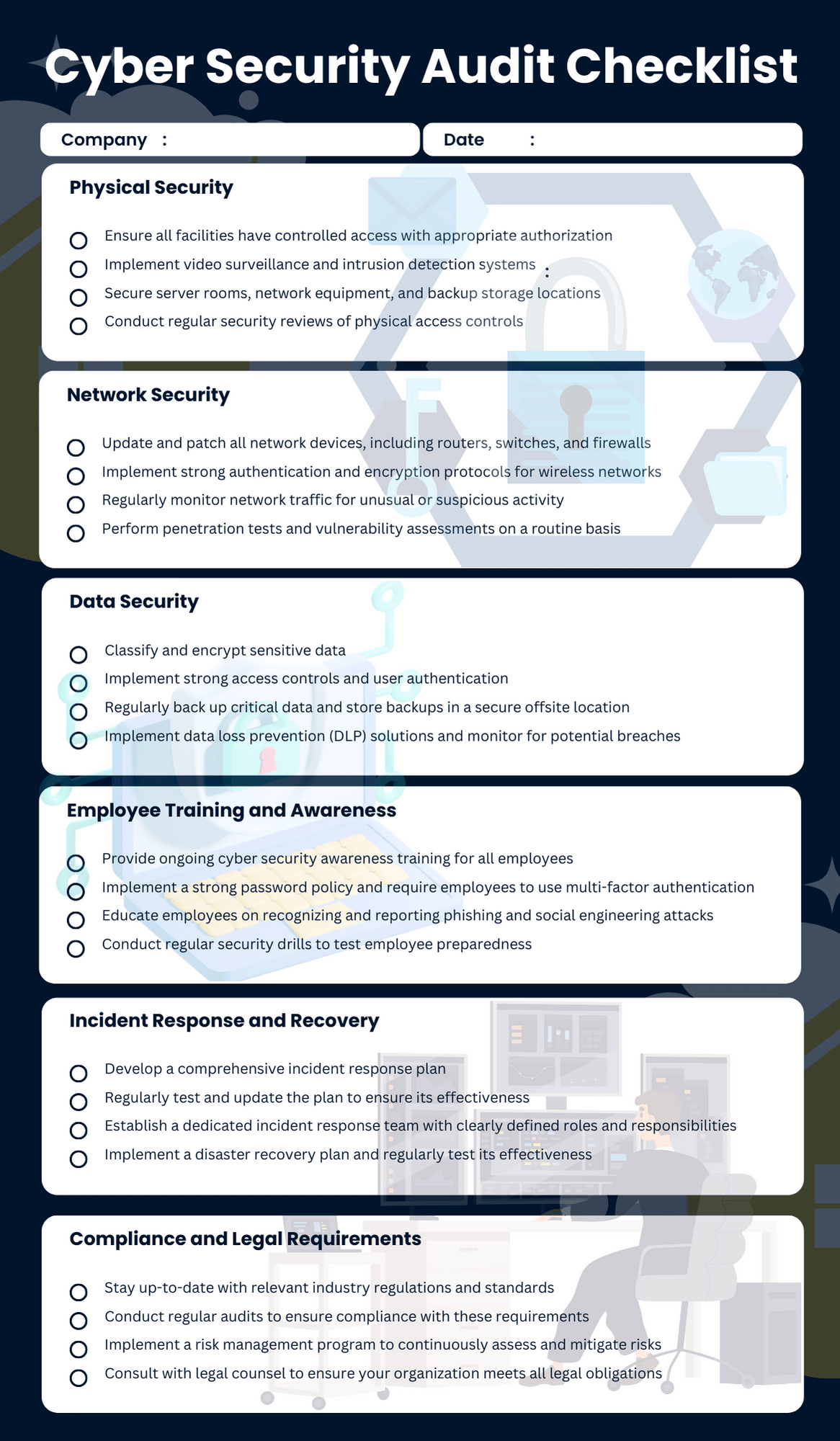
This involves evaluating your organization’s overall security policies, procedures, and governance framework. It ensures that these documents are up-to-date, comprehensive, and effectively communicated to all employees.
A vulnerability assessment identifies weaknesses in your systems, networks, and applications that could be exploited by attackers. This includes scanning for outdated software, misconfigurations, and other common vulnerabilities.
Penetration testing simulates real-world cyber attacks to evaluate the effectiveness of your security controls. This provides valuable insights into how an attacker might gain access to your systems and data.
Auditing your access controls verifies that only authorized personnel have access to sensitive data and systems. This includes reviewing user permissions, password policies, and multi-factor authentication implementation.
Analyzing your incident response plan ensures that you have a well-defined process for detecting, responding to, and recovering from cyber security incidents. This includes testing the plan through simulations and drills.
Preparing for a Cyber Security Audit
Clearly define the scope and objectives of the audit. This ensures that the audit focuses on the most critical areas and delivers the most valuable insights. Determine what systems, data, and processes will be included in the assessment.
Assemble a team of internal stakeholders from various departments, including IT, security, legal, and compliance. This collaborative approach ensures that the audit covers all relevant aspects of your organization’s operations.
Gather all relevant documentation, such as security policies, procedures, network diagrams, and incident response plans. Having this documentation readily available streamlines the audit process and provides auditors with the necessary information.
Identify and prioritize your most critical assets, such as sensitive data, critical systems, and key applications. This helps auditors focus their efforts on protecting the most valuable resources.
Communicate the importance of the audit to all employees and encourage their cooperation. This ensures that everyone understands the purpose of the audit and is willing to provide the necessary information and support.
Types of Cyber Security Audits
These audits focus on your organization’s adherence to regulatory requirements, such as GDPR, HIPAA, and PCI DSS. They ensure that you are meeting the legal and industry standards for protecting sensitive data.
A technical audit assesses the security of your systems, networks, and applications. This includes vulnerability assessments, penetration testing, and security configuration reviews.
This type of audit evaluates your organization’s overall security posture, including policies, procedures, and incident response capabilities. It provides a comprehensive assessment of your security readiness.
A web application audit focuses on the security of your web applications, identifying vulnerabilities such as SQL injection, cross-site scripting, and authentication flaws. This helps protect your web applications from attackers.
A cloud security audit evaluates the security of your cloud infrastructure and services. It ensures that your cloud environment is properly configured and protected from cyber threats.